Archived Blog
This Month in the Threat Webscape
12.08.2008 - 12:00 PMMonth of November 2008
This month we observed a huge decrease in spam numbers as the Web hosting company McColo, a major cyber-criminal safe haven, was depeered by its neighbors. The blackhats, however, proved their resilience. They managed to resurrect their zombies, though spam levels did not return to peak levels this month.
On a brighter note, Ziff Davis Enterprise's Baseline magazine recognized Stephan Chenette and the crew at Websense Security Labs among the top 10 researchers making a difference in the world of security!
Quick announcement: Follow us on Twitter for up-to-the minute bite-sized updates on what's new around the 'net block.
Follow our This Month in the Threat Webscape blog series to stay abreast of emerging Web threats.
Browser-based exploit GDP continues to rise
All major browsers were affected by vulnerabilities this month, spurring continued growth in the malicious underground economy. For the non-Microsoft crowd:
- Firefox: 4 critical vulnerabilities from the laundry list of patches (MFSA 2008-52, MFSA 2008-53, MFSA 2008-54, MFSA 2008-55)
- Safari: At least 5 important vulnerabilities that can be exploited from the Web (CVE-2008-1767, CVE-2008-3642, CVE-2008-3623, CVE-2008-2332, CVE-2008-2327)
- Chrome: 2 "moderate" vulnerabilities that are exploitable from the web (r4188, r4827)
For the Internet Explorer folks, Microsoft did not leave you out. November's Patch Tuesday includes MS08-069, which involves XML Core Services. The MSXML Memory Corruption Vulnerability CVE-2007-0099 can allow remote attackers to specially craft Web pages to cause denial of service crashes of Internet Explorer and potentially to allow remote code execution.
There is also plenty of impact from browser helper/addons in the broader Web security landscape. Adobe Flash has just patched up a few critical vulnerabilities (CVE-2008-4823, CVE-2008-4819, CVE-2008-4822, CVE-2008-4818), of which some are exploitable from maliciously crafted Web sites.
Adobe Acrobat Reader also took a hit this month, with a vulnerability discovered by Core Security (CVE-2008-2992). The vulnerability could allow attackers to take over a computer if victims opened maliciously-crafted PDF documents. It wasn't long after the announcement that proof-of-concepts were seen in the wild (we alerted on that here).
Microsoft WhyIN-De-World (does it take so long to patch?)
Patch Tuesday this month fixes a critical vulnerability (MS08-069) in XML Core Services (used by Internet Explorer). Successful exploitation of this vulnerability could lead to the compromise of the victim's desktop. All the victim has to do is visit a malicious Web site. See our alert here for more details.
Ryan Naraine from ZDNet points out that one of the issues fixed by Microsoft clocked a whopping 7-year window of exposure. The vulnerability had effectively become public knowledge, with public discussions on mailing lists and Defcon, and integration into the hacking framework Metasploit. The behemoth Microsoft lamented its self-inflicted wounds and said that it couldn't fix the bug without rendering a large part of its code base useless, preventing itself from out-nimbling every blackhat hacker's move.
Web 2 dot uh-oh
We saw confirmation that Koobface is still making its rounds, affecting Facebook users. Users receive a malicious email that links to an infected Geocities account. After multiple redirects, a video is displayed, requiring the download of a malicious file (flash_update.exe).
Rapidshare has been targeted in an evolved DIY phishing scam. The Rapidshare phishing kit has advanced a level, introducing a much more convenient interface to allow even un-experienced phishers to deploy phishing sites easily. As reported by Dancho Danchev, the authors managed to add more trust factors to the kit by imitating the dynamic link generation in Rapidshare. The kit also enables login to an actual Rapidshare account, to avoid any suspicion.
Rogue anti-virus software is sometimes hard to distinguish from legitimate anti-malware applications, until you analyze the application and its intent. With techniques like convincing testimonials, faked award logos, and supposedly secure payment over SSL used to promote the rogue software, it's not surprising that fake anti-virus software has been found on download.com (see a report here).
Major Hits
The Brazilian embassy in India's Web site and the ECPAT NZ INC courtesy site were both infected with mass JavaScript injection code. ECPAT is a global network working to eliminate child pornography and child sex abuse.
On another note, it appears that automated ASPROX SQL injection attacks have decreased significantly in the last month. China-based injection attacks still occur, but ASPROX-related attacks are on a downswing.
Spamhaus.org listed Microsoft among the top 5 worst spam networks in November, due to continued abuse of their livefilestore service (spaces.live.com) and of Hotmail, which is used for sending spam. Websense Security Labs continues to track the techniques used by spammers to peddle their wares.
The Websense Security Labs ThreatSeeker™ Network
As we saw in last month's TMTW the window of exposure (the period during which a new virus can proliferate before adequate defenses are built against it) can sometimes be days, sometimes hours. In this timeframe, users are most at risk from new malware, both Web-based and email-bourne.
The following graph shows the percentage of malware that ThreatSeeker detected before commercial scanners in the month of November:
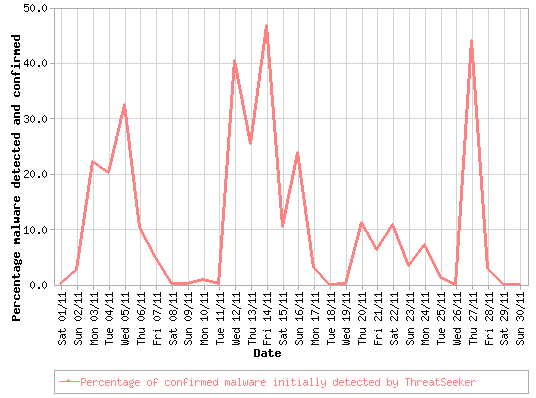
To find out more about the ThreatSeeker Network, read our whitepaper describing the Websense HoneyGrid.
Hello, ThreatSeeker. You've Got Mail!
On November 11, after the reported takedown of American ISP McColo, we saw a significant drop in spam volumes: about 50%. However, November 25 brought about a sharp rise in spam volumes—Srizbi's authors had built in a fail-safe mechanism. Read as this story unfolds, covered by Brian Krebs.

Summarizing the threats "in the mail" this month:
- 2.3 billion messages were processed by the Hosted Email Security infrastructure (an average of over 75.4 million messages per day).
- 82.8% of all email was spam.
- 78.9% of spam messages included an embedded URL.
- 7.9 million instances of 955 unique zero-day threats were stopped by ThreatSeeker before AV over the last 90 days.
- The longest window of virus exposure closed by day-zero protection from the ThreatSeeker Network was 2.7 days.
- 3.7% of all spam messages were phishing spam.
Event-driven Social Engineering
The end of the year is a traditionally a busy time, filled with cause for celebration, and spammers have tried to capitalize on that in November. We reported that users could potentially get into the festive spirit by downloading Thanksgiving-themed screen savers and end up with more than they anticipated.
Just before the end of November, spammers were already starting to use Christmas-themed lures. We have seen even more Christmas-related social engineering scams over the last few days, from the usual "you have received an e-greeting" to simple Christmas pictures with links to Web-based malicious executables.
At the start of the month, Barack Obama became the U.S. President-elect, and malware authors immediately started trying to abuse people's curiosity about the next president with a series of themed attacks.
Leaky Data Pipes
Data leaks by universities continue to trend high as 5 new schools (Harvard Law School, Texas A&M, Sinclair Community College, University of Florida, and Weber State University) reported incidents resulting in more than 360,000 total records lost. Universities continue to be the leading source of data leaks, ranking significantly higher than organizations in other industries, including finance and retail.

In 2008, there have been over 72 million records lost so far across all industries. In a dramatic increase, 27% of these records have been leaked in the last 60 days. Although 2008 began with significant data leaks occurring via outsiders, insider data loss has increased significantly over the last few months, accounting for over 23 million records lost since September.
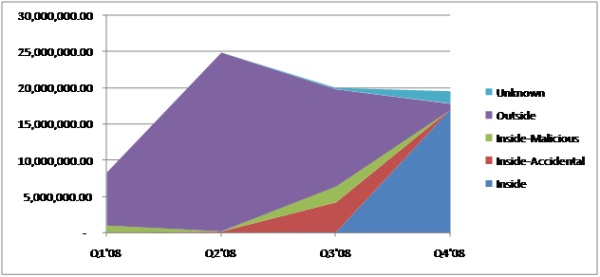
* Raw data provided by Data Loss Open Security Foundation.
Security Trends
According to researchers at UCSD, a study of approximately 350 million spam messages resulted in 28 sales (a meager conversion rate of less than 0.00001%), of which the average purchase price was almost $100. Daily revenue from Storm Worm's pharmacy campaign is estimated to be about $7000, raising to about $9500 during an active campaign. In other news, anti-virus weakness continue to gain attention, as trivial (and old) tricks to evade malware detection prove effective.
Security updates in this month's iPhone OS 2.2 solved three image-related vulnerabilities (CVE-2008-2321, CVE-2008-2327, CVE-2008-1586), two of which could lead to arbitrary code execution. This update also patches two flaws in the Web browser (CVE-2008-4231, CVE-2008-4232) that made it possible for unsuspecting users to get infected with malicious code just by visiting a maliciously-crafted Web site.
As the iPhone proves itself in the corporate environment, business users should be glad to hear that Apple patched a flaw (CVE-2008-4211) where opening a maliciously-crafted Excel file could lead to running the attacker's code.



























