Archived Blog
Spammers Abusing Microsoft Services
10.27.2008 - 9:00 AMTo summarize: for the spammers, the entire attack strategy includes more than harvesting or registering email accounts using Anti-CAPTCHA operations. It also involves operations like sending mass emails over the Internet; creating splogs and splogospheres; comment spam; infecting thousands of user machines; and stealing information. Their marketing business online is to occupy the network traffic, and also improve their current advertising model and approach to reach customers with increased success over the email, Web and Web 2.0 space. Spammers and malware authors execute their tactics with a unified strategy and constantly keep switching among those tactics, with an emphasis on improving their underground economy. The entire strategy is a continuous cycle, where every stage is an emerging trend or an execution phase inherited from the previous cycle(s).
Let us now understand how spammers and their recent developments have been targeting Microsoft services with a wide range of attacks.
Earlier this year (2008), as reported by Websense Security Labs, spammers defeated Microsoft’s CAPTCHA system targeting Microsoft’s Live Mail to sign up and create their accounts. Spammers widely used these accounts to advertise their products and services, and carry out a different range of attacks, using the trusted reputation of Microsoft’s Live Mail systems. Realizing spammers were abusing Live Mail services, Microsoft improved the Live Mail account signup and creation process, while preserving their CAPTCHA system for usability.
Spammers then shifted their attention towards Microsoft’s Live Hotmail. Spammers targeted Live Hotmail services performing streamlined Anti-CAPTCHA operations, successfully signing up and creating Live Hotmail accounts. During this operation, spammers also focused on improving their automated Anti-CAPTCHA model which provided them with faster turn-around times and increased success. The entire automated process comprised of successful account signup, CAPTCHA break, account creation, and then mass-mailing within a single operation.
Screenshot showing Microsoft's old CAPTCHA system busted successfully by spammers:

When Microsoft realized their trusted reputation was being massively abused by spammers with increasing anti-CAPTCHA capabilities, they attempted to increase the complexity of their CAPTCHA system. This time the CAPTCHA system was revised in an attempt to both prevent automatic registrations from computer programs or automated bots, and preserve CAPTCHA's usability and reliability. It has recently been observed that spammers have revisited Microsoft’s new CAPTCHA system, and have once again broken it with their new, improved and automated Anti-CAPTCHA model.
Screenshot showing Microsoft's new CAPTCHA system busted successfully by spammers:
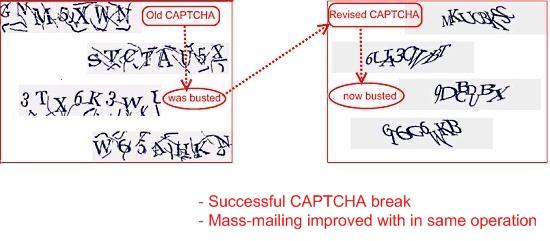
By defeating Microsoft’s CAPTCHA system, and registering Live Mail or Live Hotmail accounts, spammers clearly aim to carry out a wide range of attacks (both manual and automated) on other services with which they are integrated.
To demonstrate this, here are a few instances of recent attacks where spammers and malware authors have been increasingly using their bogus accounts on Livefilestore.com associated with SkyDrive (previously known as Windows Live Folders) online file storage service offered by Microsoft, to carry out a wide range of attacks by hosting spam content and malicious ware.
Screenshot showing spammed links on Microsoft's Livefilestore hosting spam content:
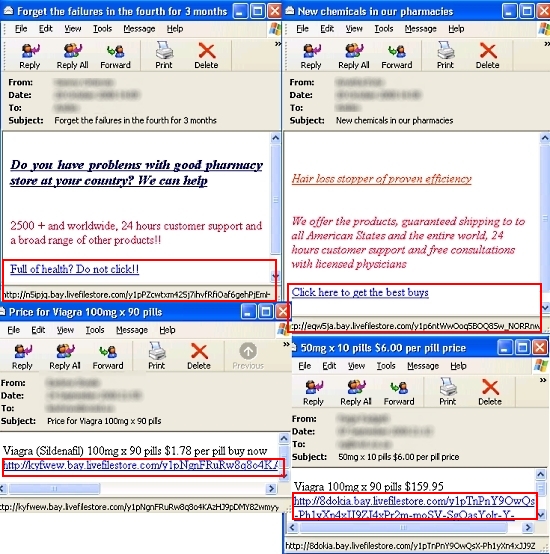
Screenshot showing links on Microsoft's Livefilestore hosting malicious ware:

Some spammers constantly work on improving their business model and building new versions; others work on improving their opportunities with their existing business model. Some of the spammers are busy harvesting email addresses to be used or sold later on, and others have come up with the idea of using them in the most effective way to advertise their products and services, and also carry out different attacks. Spammers always aim to improve the chances of success with their tactics and attacks.
Spammers have also realized that spamming ‘from’ and ‘to’ Hotmail, Live or MSN account users increases the chances of success with their mass-mailing strategy. Below are some instances where spammers have been targeting Microsoft’s mailing services.
Screenshot showing spammer botnets targeting Hotmail, Live, MSN-based email addresses:
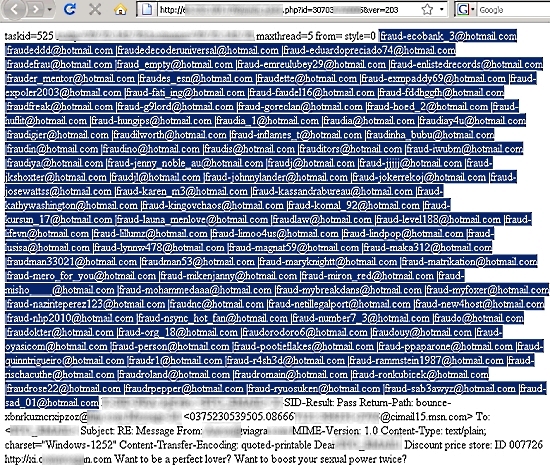
Screenshot showing 'to' and 'from' Hotmail, Live, MSN-based spam campaigns:

All of these tactics clearly represent the execution phases of many spammers' recent strategies. This entire ecosystem targeting Microsoft services shows the spammers' mindset of developing an efficient system that can use Microsoft's trusted reputation to instigate successful spam advertising campaigns. Spammers and malware authors have also been targeting other popular Email, Web and Web 2.0 service providers with similar attacks, to successfully carry out their operations.
Security Researcher: Sumeet Prasad



























