Archived Blog
This Month in the Threat Webscape
11.07.2008 - 5:36 PMMonth of October 2008
This month, major Web 2.0 properties like Facebook, Bebo, Yahoo, and Google continue to be plagued with problems by malicious 'net scum, and the malicious underground economy continues to boom as stock markets tank. The Matrix's "architect" (or just, "father of the Internet") Vint Cerf explains why, architecturally, the Internet will not be entirely free from the malicious underground. In other much anticipated news, Google's "iPhone-killer" Android makes a splash this month, complete with a drive-by browser vulnerability.Follow our This Month in the Threat Webscape series to stay abreast of emerging Web threats.
Web 2.0 major hits
Facebook continues to be plagued with malicious messages containing links to malware, but proxied through Google Reader and Google Picasa. In sync with one of the Web 2.0 value propositions (continuous sharing and remixing of data), the ability to share links from Google Reader and Picasa is a feature, not a flaw - but it is no doubt being abused for malicious activity. The fact that the content is "shared from a friend" and hosted from Google (at least by proxy) deals a blow to reputation-based security filters.
Unemployment rates have been a closely-watched metric in these uncertain times, and while Yahoo fretted over losing its advertising deal with Google, malicious hackers have been busy phishing for Yahoo user accounts by exploiting a cross-site scripting (XSS) flaw on Yahoo's property for job seekers - Yahoo HotJobs. Visiting the malicious page was all one needed to fall prey (no need to type password, etc.).
In social-networking news, baddies continue working downwards on the list of top social-networking sites by market share. We've previously reported many times on MySpace (ranked #1) and Facebook (ranked #2). This month, Dancho Danchev at ZDNet reported thousands of bogus profiles on Bebo (ranked #3), also referencing our previous report on Bebo.
When a large reputable company acquires a lesser known company, do they "carry over" their Web site security best practices? This month, Adobe's Serious Magic site fell prey to an SQL injection by the Asprox botnet.
Microsoft
As the most famous product that Microsoft is known for (Windows) remains the market share leader and operating system of choice for employees by corporations globally - so do the (infamous) threats targeting Microsoft continue. Patch Tuesday shines a light on more Web threats, including six vulnerabilities for Internet Explorer with a rating of "critical" and three MS Office Excel vulnerabilities (also rated "critical").
Also special this month was an out-of-band patch (a patch that's outside of the "Patch Tuesday" cycle), testifying to the severity of a flaw in Wind-uh-ohs so critical that Microsoft could not wait until the next patch cycle. The vulnerability (CVE-2008-4250) allows malicious hackers to write a worm (self-propagating malicious code without need for any user interaction), by crafting a special RPC request.
Browsing for dirt
Opera claimed the spotlight this month for making the most security headlines with its many patched (and still unpatched) flaws. On Opera's list:
- A specially crafted URL may crash the browser and could lead to execution of malicious code. Rating: Extremely severe
- Cached Java applets could be used to steal sensitive information. Rating: Highly severe
- Feed preview can reveal contents of unrelated news feeds. Rating: Highly severe
- History search can reveal browsing history. Rating: Extremely severe (Proof-of-concept here)
- Fast Forward cross-site scripting (XSS). Rating: Highly severe
In other browser news, Google's Chrome was found to be susceptible to a combination of two known vulnerabilities from WebKit and Java (click here for proof-of-concept). The flaw allows the downloading and automatic execution of a JAR file without further interaction. Chrome is also found to be vulnerable to an address bar spoofing flaw, to the delight of phishing attack groups around the world.
Rock phish to parallel the economic crisis
On-going global financial crises have been proving an encouraging factor to Rock-phishers to continue their phishing attacks targeting various financial sectors to steal user account credentials. The phishing authors continue to push several sophisticated crimeware packages that get silently installed on the victim's PC. The classical bullet-proof network infrastructure using the fast-flux concept continues its attacks, recent targets being Suntrust, Bank of America, and Ocean Bank.
Hello, ThreatSeeker. You've Got Mail!
The ThreatSeeker™ Network discovers many malicious applications being circulated via email, drive-by downloads, exploit code, and other mechanisms employed by ever more creative malware authors. One set of malicious attachments that have been distributed by legitimate-looking email lures are those of the so-called UPS/parcel/invoice spam, which is a continuing campaign through October. We frequently see that the ThreatSeeker network is able to protect our customers from these malicious applications in advance of anti-virus signatures.
The following graph shows the percentage of other malware detected by ThreatSeeker before commercial scanners:
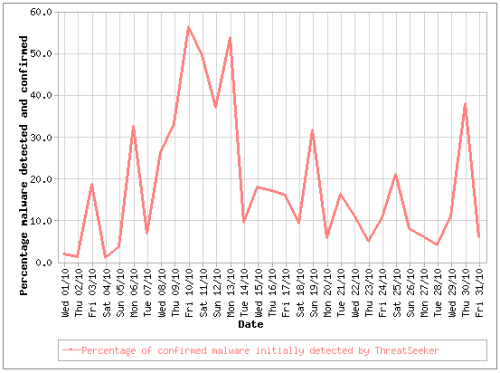
The "window of exposure" table below shows the number of occurrences of malware caught by ThreatSeeker and the time taken before the first anti-virus signatures triggered:
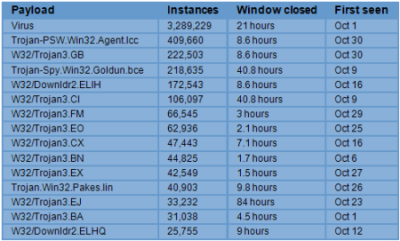
You can find out more about the ThreatSeeker Network by reading our whitepaper describing the Websense HoneyGrid.
Spammers busted? Spam gone?
"The Federal Trade Commission announced they shut down the operations of a global spam network that advertised fraudulent drugs and products that accounts for nearly one-third of the world’s spam messages," as per online news reporters. In contrast, some news sources also reported that the spam relating to Health and Services is still continuing. This implies that the spammers’ mass-mailing underground economy is distributed. Mass-mailing online still emerges as a strong potential for online marketing of their products and services.
Security Trends
Web threats, now customized for phones
The first incarnation of Google’s answer to the iPhone (Android), launched by T-Mobile, made a huge splash this month. Coinciding with the splash was news of a vulnerability where the Android phone may be compromised if the users visited a maliciously crafted Web page. Just a few weeks prior, Georgia Tech Information Security Center (GTISC) reported that mobile malicious code that turns cellphones into bots would be one of the next big threats.
Protect yourself, the Internet is one big free-for-all
Vint Cerf, the "father of the Internet" says that on the Internet, "It’s every man for himself. In the end, it seems every machine has to defend itself. The Internet was designed that way." He believes that the power of the Internet is from its openness, and that like every medium, it is open for abuse. Vint also warns that while taking this openness away would help curb malicious activity, it would also stifle innovation (none of the Web 2.0 goodness would exist). Thus, find a way to deal with the bad stuff - because the father himself isn’t going to fix it, even if he could.
Worm Times: Morris turns 20!
This month, the Morris worm marks its 20th birthday since it first wreaked havoc across the net, and Microsoft decided to commemorate this occasion by patching a critical "wormable" vulnerability in Windows. Patch announcements are always a double-edged sword, because they not only inform users to update quickly, but also signal the bad guys that there’s an exploit to be profited from. The victims are those who stay out of the loop and don’t realize there’s a need to patch. (Grab our feed to stay informed!)
Does the health of the malware economy run countercyclical to the global economy?
As the stock market blood-bath continues and the world economy dips, the malware economy continues to thrive. Actually, there is no solid evidence that the underground economy takes a hit when the real world does well, so there’s a chance that the bad guys are hitting their revenue projections, independent of the macro-economic trend. As tempting as they may be for institutional long-term investors, Websense security researchers strongly maintain a "sell" recommendation on the malicious hackers. (We'd offload that junk in a heartbeat.)



























