Archived Blog
This Month in the Threat Webscape
12.07.2009 - 5:27 PMMonth of November 2009
Major hits
The official Web site of the Singapore Foreign Exchange Market was compromised and injected with malicious code via an iframe redirector that drops a malicious file onto the victim's computer.
Web 2 dot uh-oh
The Torpig botnet is employing what appears to be a novel technique for escaping detection. It computes a drive-by-download domain by combining the current date with search trend data from Twitter. A more in-depth analysis of the botnet can be found here.- Getting into the holiday spirit by switching to a Christmas theme. The botnet also experimented with serving client-side exploits, though this approach appears to have been abandoned for now.
- Using Google Reader to host pages that themselves host fake videos that prompt the user to install malware.
- Attempting to force users of infected computers to break Facebook CAPTCHAs. Users are presented with a dialog that threatens to shut down their computer if they do not complete a CAPTCHA.
- Their most recent update is a "visual social engineering element" strategy that adds descriptive domains after the original link, e.g. bit.ly/588dmE?YOUTUBE.COM/ea05981d43. To help protect against these types of attacks, bit.ly has recently partnered with Websense.
Browsing for dirt
Another “silent patch” has been distributed by Google for its Chrome browser after the discovery of a pair of vulnerabilities. Details of both have been kept undisclosed until a majority of users are up to date with the fix. One of the vulnerabilities was ranked “high-risk” due to its threat of arbitrary code execution.
Two security holes is bad, but three is surely worse. Opera released the newest version of its browser, 10.10, patching three “extremely severe” vulnerabilities. They include the possibility of heap buffer overflows, the leaking of error messages onto unrelated sites, and an undisclosed third one. We're wondering what that one was about.
If two is bad and three worse, what can we say about seven? Exactly such a number of security flaws have been patched in the newest Apple Safari 4.0.4. Users of both Windows and Mac operating systems have been exposed to a wide range of malicious hacker attacks.
Several security flaws have been patched in the newest version of Adobe Shockwave Player, including a “run malicious code” bug and other similarly juicy ones.
We have already had two, three, seven and several holes, but how about 50? To be more precise, 50 million files have been exposed to potential leakage of sensitive information due to Microsoft's bug in the Internet Explorer PDF exporting function. All such generated documents reveal the file's full storage path. What else have we to ask for?
Microsoft
And the new Windows 7 seems not to be very safe. A recent test reveals that 8 of 10 malwares bypassed the default UAC(user access control). Also an SMB exploit that can cause denial of service in Windows 7 and Windows Server 2008 R2 has been confirmed by Microsoft.
There is also a zero day exploit that can affect IE 6 and 7 on fully patched Windows XP SP3 systems. This exploit will be triggered when retrieving certain CSS/STYLE objects via the "getElementsByTagName()" method. The attacker could execute arbitrary code by tricking a user into visiting a mal crafted web page.
Hello ThreatSeeker. You've got mail!


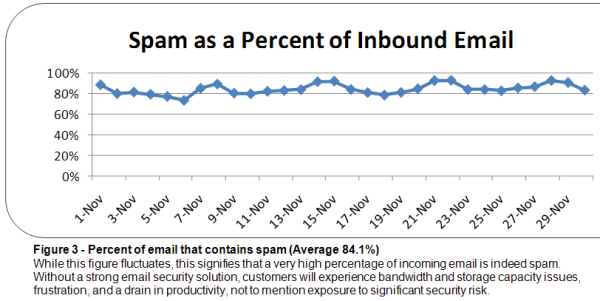

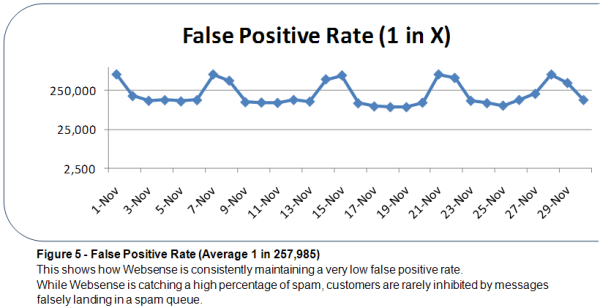
So long, and thanks for all the phish
The phishing email redirects the victim to a spoofed page that harvests all the information the victim provided the card-issuing bank at the time of sign up for the credit card.
PandaLab has warned against a facebook phishing attempt that aims to harvest facebook credentials. Once the victim enters a username and the password, he or she is redirected to an error message claiming an "incorrect email/password combination".
Security Trends
The first iPhone worm was launched in the beginning of November in Australia. The worm, written by a hacker calling himself "ikee", changes the lock background wallpaper to an image of Rick Astley if the iPhone installed SSH with the default password. Furthermore, a more malicious hacker could take the code written by ikee and adapt it to have a more sinister payload.Man-in-the-middle attacks against several smartphones over insecure Wi-Fi networks is taking place everywhere. Hackers can sniff on several mobile devices using the publicly available SSLstrip tool if the smartphone owner accesses a Web site over a public Wi-Fi network.
To wrap it up, "ransomware" typically encrypts some of the user's personal files, or locks the display at system startup. Now, users may stumbled upon a new piece of ransomware that blocks Internet access until a fee is paid via SMS.
Thanks to the following contributors for this month's roundup:
- Sebastian Becerra (Security & Technology Research)
- Lei Li (Security & Technology Research)
- Ulysses Wang (Security & Technology Research)
- Ivan Sabo (Security & Technology Research)
- Saeed Abu-Nimeh (Security & Technology Research)
- Jay Liew (Security & Technology Research)



























