Alerts
Malicious Facebook Password Spam
Date:10.26.2009
Threat Type: Malicious Web Site / Malicious Code
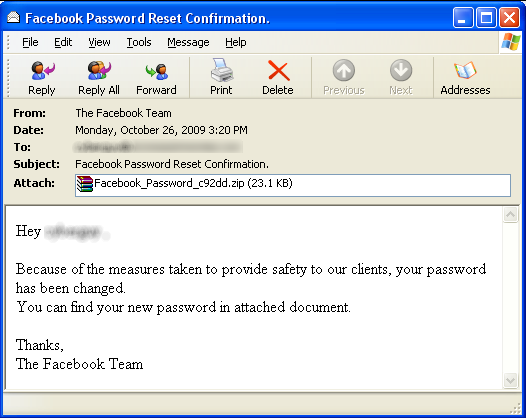
Websense® Security Labs™ ThreatSeeker™ Network has discovered a new wave of malicious email attacks claiming to be a password reset confirmation from Facebook. The From: address on the messages is spoofed using support@facebook.com to make the messages believable to recipients. The messages contain a .zip file attachment with an .exe file inside (SHA1:
The malicious exe file connects to two servers to download additional malicious files and joins the Bredolab botnet which means the attackers have full control of the PC, such as steal customer information, send spam emails. One of the servers is in the Netherlands and the other one in Kazakhstan.
Screen shot of malicious message:
Websense® Messaging and Websense Web Security customers are protected against this attack.


























