Archived Blog

Figure 1: Stephan Chenette's FireShark RSA Talk 
Figure 2: Dan Hubbards's Threats to Cloud Computing RSA Talk
I presented the details of a Web security Firefox plugin that I will soon be releasing open sourced called FireShark. The plugin helps in visualizing various Web attacks such as mass URL injection attacks like Gumblar, Beladen, or Nine-ball. I have to personally thank Wladimir Palant, who you should know from his development effort on a plugin called AdBlock plus. Wladimir was instrumental in offering tips to Firefox plugin writing. Thanks Wladimir!
Essentially FireShark is a local plugin that, when used in a clustering architecture, can become a very powerful mechanism in visualizing the malicious Web. In my presentation, I shared several real-life scenarios of compromised Web sites. On one occasion, FireShark mapped out one particular malicious community that later, when operation b49 was exposed, uncovered that many of the hosts involved were also Waledac spamming domains. FireShark made it easy to see that these domains were responsible for acting as control points, redirecting users from legitimate compromised Web sites to landing pages serving rogue antivirus. More so, FireShark's post processing mechanism could conduct analysis on compromised machines, intermediary machines and the final landing pages, so that not one piece of information was left unknown. This includes the original source code, the de-obfuscated source code (final DOM view), and any window prompt or malware that the user is optionally asked to download and install. This is useful for one Web site, but FireShark does this for millions of sites every day. By correlating all the data, FireShark is able to take the normalized data and link various previously assumed unrelated attacks.
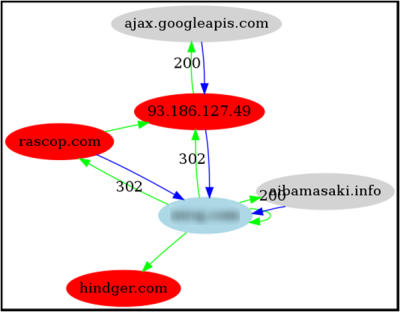
Figure 3: A Web site that was compromised and part of a small malicious community, graphed with GraphViz from FireShark output

Figure 4: Stephan Chenette (me) speaking at RSA
I sat down with Rob Lemos in an interview while at RSA; so if you're interested in knowing more about FireShark until it's released, you can read the article here.
Days before my presentation, Dan Hubbard co-presented with researchers from ZScaler outlining some of the current top cloud computing threats. Dan's presentation as well as all presentations given at the Cloud Security Alliance conference at RSA can be found here.
Here are a few images of the conference. If you were there, you know that our Websense booth was not easy to miss; it was probably the largest and most impressive booth I've ever seen.
Principal Security Researcher: Stephan Chenette































