Archived Blog
iPhone Blackhat SEO Poisoning Leads to Total Security Rogue Antivirus
09.28.2009 - 9:00 AMThe Apple iPhone which is one of the most popular smart phones on the market, announced last week the release of MMS on newer versions of the iPhone. Attackers reacted to this news by poisoning search engine results to lure iPhone users to malicious and fraudulant sites that were under their control.
When Google is used to search for terms related to iPhone SMS information, malicious URLs are returned as high as the sixth result. When a user clicks an affected search-result link, they are redirected to a Web site advising that their machine is infected with malicious threats. It then proceeds to offer rogue or fake AV software.
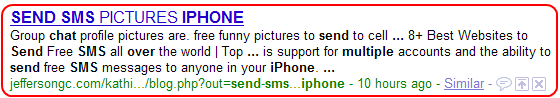
Google Results
Figure 1) Google results

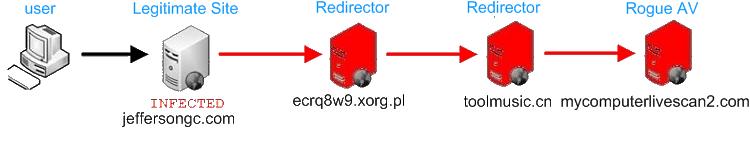
The Infection Trail
If a user clicks on a link controlled by attackers in this scheme, they are redirected through a series of sites via 302 redirects. The final landing page attempts a scareware technique of warning the user that they have been infected with malware and must clean their system. The user is then prompted to download fake antivirus software.
Figure 2) Flow of 302 redirects from Blackhat SEO site to Rogue AV site
Rogue AV Site in Action
Figure 3) Rogue AV site

Figure 4) Fake Rogue AV threat scan
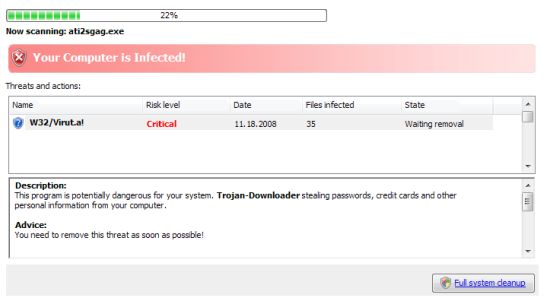
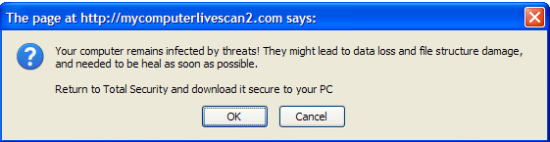
Figure 5) Rogue AV site completing fake threat scan:
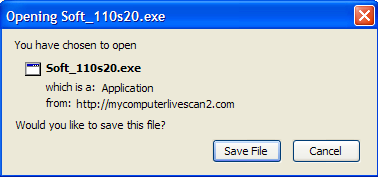
VirusTotal Results
As is the case with all Rogue AV binaries, detection within traditional AV software is very low.
Figure 7) VirusTotal detection of Rogue AV software
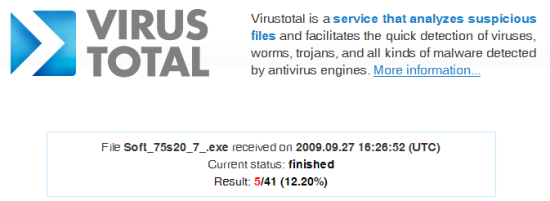
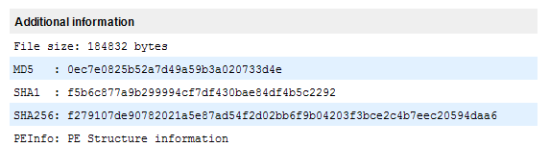
Figure 8) VirusTotal additional information
The Who, What and Where
In this particular iPhone Blackhat SEO attack, the following hosts are involved:
- hxxp://jeffersongc.com
- hxxp://ecrq8w9.xorg.pl
- hxxp;//toolmusic.cn
- hxxp://mycomputerlivescan2.com
Using Robtex and various other tools, we can gather public information about these hosts. One interesting fact we found is that the domain hosting landing page serving the rogue AV was created on September 23rd 2009 (within the last week), and the other domain involved was registered minutes before. We can also see that two of the domains involved share the same IP address.
- hxxp://jeffersongc.com
- hxxp://ecrq8w9.xorg.pl
- hxxp;//toolmusic.cn

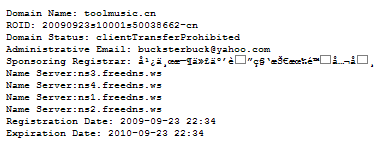
- hxxp://mycomputerlivescan2.com
Conclusion
The use of Blackhat SEO leading to Rogue AV will only increase in the upcoming year. This scare tactic has proved to be a very successful method of social-engineering users into installing software onto their computers and tricking them into paying for it.
Websense Messaging and Websense Web Security customers are protected against this attack.
Principal Security Researcher: Stephan Chenette



























