Archived Blog
Barack Obama's Site Leading to Trojan
01.26.2009 - 9:00 AMWebsense Security Labs™ ThreatSeeker™ Network has detected that malicious hackers have registered multiple bogus user accounts on My.BarackObama.com (an online community for citizens to rally behind President Obama), in order to spread malicious code around the Web. A My.BarackObama.com social-networking account empowers the user with tools to join groups, raise funds, and even create his or her own blog. The option to create your own blog is a common feature provided by most of the popular Web 2.0 social sites today, driven by user-generated content.
In the Obama campaign, malicious hackers created blogs on My.BarackObama.com with a fake YouTube image, enticing visitors to "Click here to see movie".
Screenshot of the My.BarackObama blog post:
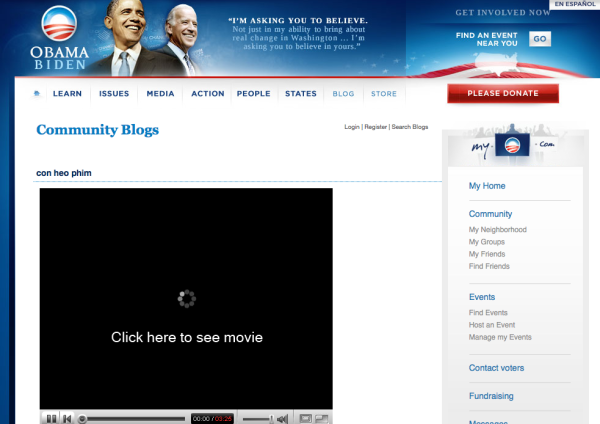
Clicking on the link leads to a Web site using YouTube's template for viewing online videos, filled with pornography.
Screenshot of the malicious online video Web site:

Clicking on the video to view results in the Web site prompts the browser to download a supposedly required video codec, which is really a malicious Trojan .exe.
Screenshot of the malicious online video site, peddling the download of a Trojan masquerading as a codec:

But the malicious campaign doesn't end there. BarackObama.com is a highly visible, reputable, and popular Web site, with an Alexa ranking of 872 (at time of writing), with almost 9,000 other sites linking to it (according to Alexa). The malicious hackers have been spraying these BarackObama.com URLs all over the Web by injecting them onto blog comment forms, and various user-generated content management systems commonly used by Web 2.0 sites.
Screenshot of Web 2.0 sites that host user-generated content injected with the BarackObama.com link:

Visitors who double-click on this downloaded .exe will be infected with a Trojan. At the time of this writing, the malicious code has almost a 35% detection rate by the major anti-virus vendors (SHA-1: 7e1e623cdae2aba83aecaa2380133b3ccb4f1193). We acknowledge that this has been mentioned before, but now that President Obama has officially been sworn in, and with the new administration's efforts to "expand and deepen this online engagement", we can be sure that the frequency and intensity of malicious campaigns aimed at anyone seeking to engage with the President online will only increase. The malicious hackers will also seek new ways to abuse Web 2.0 functionality on any of the new administration's online properties.
Just prior to the inauguration, US-CERT reported increased spam and phishing sites aimed at luring anyone searching for information on the historical event. We are monitoring this threat, and the ThreatSeeker Network can confirm the US-CERT report. Here are two screenshots of more malicious activity centered around the Presidential Inauguration.
Screenshot of Web sites infected by the malicious campaign:
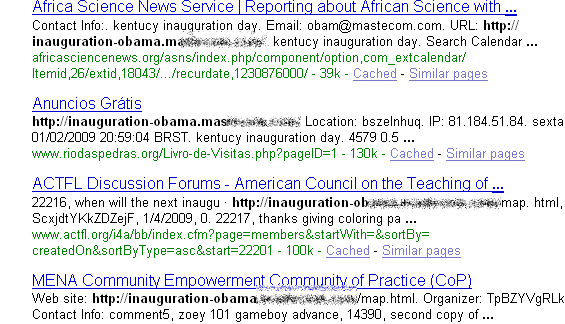
Screenshot of Web sites infected by the malicious campaign (different malicious hub):

Websense® Messaging and Websense Web Security customers are protected against this attack.



























