Archived Blog
This Month in the Threat Webscape
01.14.2009 - 6:00 PMMonth of December 2008
This month we observed the malicious hackers' well-oiled machine at work, capitalizing on the opportunity made possible by a Microsoft Internet Explorer zero-day to claim even more victims by spreading exploits for this vulnerability via a mass SQL injection attack. The Web plays a crucial role in amplifying this attack, which, without the speed at which this malicious code can spread, would be bounded by how fast one can take a diskette from one computer and plug it into another.Aside from just being a vector, the Web also comes with its own set of security challenges: Google Ads that linked to malicious Web sites, XSS vulnerabilities on Facebook and American Express, more major browser holes being plugged, more people not patching their Windows desktops (~98%), and even more spam jam-packed with malicious-(bad)ness. With the proliferation of blogging, malicious comment spam uptick is also to be paid its due-diligence.
Read on for a recap of what's hot in the world of Web Security in December of '08.
Web 2 dot uh-oh
A total of 4 cross-site scripting (XSS) vulnerabilities were discovered on Facebook this month, affecting various pages, such as the developers page, new users registration page, iPhone login page, and applications page. This is a flaw inside of Facebook's code. In other Facebook security news, the Koobface worm makes a comeback. This not a flaw in Facebook's code, but a campaign by a malware group. Talk about internal and external threats!
With the Koobface worm's "pilot program" a success, the gang behind Koobface have begun the next stage of their go-to-market strategy, now marketing the worm that made its initial debut on Facebook, to now target users of MySpace, Bebo, Friendster, and others. Talk about a carefully planned product launch! Hot on the heels of the Facebook flurry, the Nigerian 419 scammers have now found another use of the Internet in Nigeria—to reel in even more advance-fee fraud victims.
Major Hits
This month, we warned about Google Ads that, although they led to reputable-looking sites (like CNet's Download.com), they really served as a distribution channel for rogue software vendors to peddle their wares. The site masquerading as Download.com displayed the words "Tested spyware free" next to the download link, but that was far from the truth. The popular decompressor WinRAR provided was packed with malware, and victims would have their machines held ransom. More details in our analysis here.
Reports of multiple cross-site scripting (XSS) flaws on American Express's Web site surfaced this month. One of the flaws involved input validation, whereby an attacker could collect session cookies and inject arbitrary malicious code to be loaded by the victim's browser. A proof-of-concept (PoC) exploit was created to show how a malicious Web site could steal a user's americanexpress.com cookie after logging in with their username and password.
Major online bill-pay provider, CheckFree, had control of its Web site seized by malicious hackers, who then configured to redirect CheckFree's customers to a malicious Web site hosted in Ukraine, that tried to install malware on the visitors' computers. CheckFree claims it has more than 24Mil customers, and Gartner said CheckFree controls 70-80% of the U.S. online bill-pay market. Among the bills that can be paid through CheckFree are: utility bills, mortgage, insurance, and loan payments.
Microshaft
On Patch Tuesday, Microsoft plugged memory corruption holes in Internet Explorer (MS08-073: CVE-2008-4258, CVE-2008-4259, CVE-2008-4260, CVE-2008-4261), as well as various vulnerabilities in its graphics API that were exploitable from the Web (MS08-071: CVE-2008-2249, CVE-2008-3465).
But let's dive into what really stole the show this month of Dec '08: A 0-day in Internet Explorer (MS08-078: CVE-2008-4844) surfaced almost immediately after the patch cycle that got the folks in Redmond scrambling for an answer. Not surprisingly, soon after the word got out, malicious hackers were discovered to have included this latest-and-greatest exploit in their existing "portfolio" of browser exploits (nicely packaged in a .js file) for use in a massive SQL injection of hundreds of thousands of Web servers. We have a technical analysis of this vulnerability posted on our blog, here.
Browsing for dirt
All major browsers had some form of security issues reported this month. Firefox saw 3 "critical" (MFSA 2008-69, MFSA 2008-68, MFSA 2008-60) and 1 "high" (MFSA 2008-65) impact security advisories (among a laundry list including other fixes). MFSA 2008-60 could be exploited to run an attacker's code of choice, whereas MFSA 2008-65 could allow a malicious Web site to steal private data from users.
Opera's 9.63 security update includes 2 extremely severe (1, 2) and 3 highly severe (1, 2, 3) patches, of which the most serious compromise would allow an attacker to run their malicious code of choice (e.g., a Trojan), should the victim accidentally visit a malicious Web site—no explicit user-interaction required, other than surfing to the malicious URL (or even just by visiting a big name reputable site that was injected with malicious code).
Apple's picnic basket of shiny objects for OS X includes CVE-2008-3170, a peanut-butter filler to patch Safari's Cross-site Cooking crack (drop it like it's hot!)
In other news, a password-stealing malware tries to pass as a Firefox plugin; a study exposed that all major browsers have been mishandling passwords; and Adobe confirms ElcomSoft's statement that password-protected documents in Acrobat 9 are actually easier to crack than in Acrobat 8 ("it's a trade-off, people!"). We agree, security is usually at odds with functionality/ease-of-use—but we're working hard to allow the enterprise to consume Web 2.0 (sans the downside).
Hello ThreatSeeker. You've got mail!
Threats “in the mail” this month:
- 2.9 billion messages were processed by the Hosted Infrastructure, or an average of over 94.5 million messages/day
- 88.1% of all email was spam – a notable increase from 82.8% last month
- 88% of spam included an embedded URL
- 5.4 million instances of 709 unique zero-day threats were stopped by ThreatSeeker before AV over the last 90 days
- 2.81% of all spam messages were phishing spam
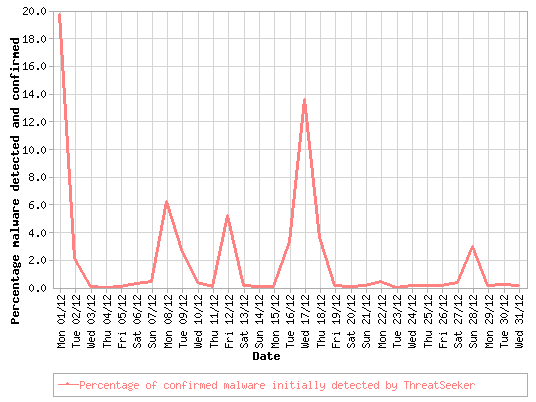
As we reported in our This Month in the Threat Webscape roundup for November 2008, the effect of disconnecting the notorious, cybercrime-friendly ISP, McColo, was significant, directly attributing to a drop in spam volumes.

When it comes to the web, there's no single bigger annoyance than spam. And while 2008 saw a promising blow to an endless sea of spam-related operations and resulting junk emails, we expect that levels and the ways spam is distributed will rise in 2009.
Spam or Ham
The close of 2008 involved cleaning up and shuttering some of the most notorious spam networks on the planet. It was only a matter of time for spam volume began to skyrocket again, with the main botnets using that ISP for their command and control locations regaining their strength by migrating to new hosting locations.
Already several new breeds of spam botnets—massive groups of hacked PCs used for spamming—have risen from the ashes, employing a mix of old and new tricks to all but ensure a steady flow of spam into email boxes everywhere for many months to come.
Websense Security Labs has been constantly monitoring different tactics used by spammers, and has been closely observing trends and changes in different spam campaigns sent by spammers locally as well as globally. Early December, realizing the holiday season was on its way, spammers used famous brand names – McDonald’s and Coca-Cola based social engineering spam to infect users with malicious code, sent in as attachments in emails.
Spammers have also been experimenting with localized spam campaigns confined to a region, themed with local incidents to increase their attack chances. A couple of such instances were discovered and alerted by Websense Security Labs. Spammers targeted a Brazilian region with spam relating to natural disasters in the state of Santa Catarina. French users were also being targeted by spammers with a spam themed with a Fake Microsoft Advisory.
A few other attacks were also reported relating to Windows Live Messenger spoofs sent via email, in Spanish, which led to malicious payload from a defaced Web site that had a poor Antivirus detection rate. Spammers have also excelled in targeting users globally with spam campaigns themed with Christmas festive seasons greetings using visual social engineering tactics to spread malicious code.
Leaky Data Pipes
In Review: 2008 Data Loss Trends
2008 was a wild ride for many organizations that continue to struggle to keep their data secure. Here’s an analysis of the data loss incidents on record for 2008:
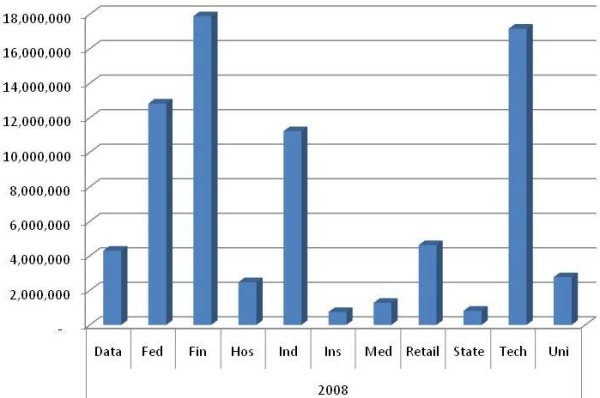
Businesses (B2B and B2C) beat out education, government, and medical fields (see Chart 1) as the leading sector for data loss, with a combined loss of over 55 million records. The biggest industry losers were finance, technology, federal, and manufacturing. Together, they account for over 77% of all records lost in 2008 – over 55 million (see Chart 2). Retailers showed a decline in the number of leaks and records lost, year over year, in part because of the massive amount of data loss they incurred in 2007 with such incidents as the TJX breach. Data loss from healthcare organizations and insurance providers rose by 126% and 140% respectively, year over year.
Stolen/lost laptops, hacks, over the Web, and email were among the top vectors of data loss in 2008 (see Chart 3). Together, they accounted for more than 171 data loss incidents (55%) totaling over 15 million records lost.

2008 had fewer high profile data leaks, but maintained the same volume over 2006 and 2007. The downturn in the economy, cutbacks in personnel, the failure of corporations, and decreased security investments have created the perfect circumstances for significant data loss in 2009. Organizations will be forced to do more with less, and their dogged determination to hit revenue targets will increase their tolerance to risk.
Special thanks to the Data Loss Open Security Foundation for providing raw data. For additional insight and analysis on data loss prevention, visit ondlp.com
Israel Gaza Conflict Cyber Warfare
The Israeli-Palestinian conflict has escalated to the cyberspace realm. Precedent conflicts, like in Estonia and Georgia-Russia demonstrate how these kinds of conflicts are due to escalate to cyber space. Reports and evidence have been received, and are still being gathered, showing different attacks, such as Web site defacements and DDoS, as the conflict continues.
One of the interesting attacks initiatives in the conflict was a Web site established by a group of Israeli students, which offers to download a file named PatriotInstaller.exe to aid in a collaborative patriotic effort against Hamas Web sites. Once installed, the file turns the computer into a bot which may help in issuing DDoS attacks, but also effectively gives someone else control over the system—so the file's integrity is questionable. It has also been found that the same site was hacked and injected to host malicious files, which don’t have the same "good intentions" as the original download. Recent malicious spam campaigns have also started to use the conflict as a social engineering tactic.
Security Trends
Microsoft's Google-killer, Live Search, finally catches up with Google and Yahoo!—by adding friendly "malware" labels on search results it deems dodgy. Google began to realize how serious of a threat malicious Web sites are, and added warning labels beginning in early 2007. Yahoo! followed suit about half a year ago. And it's about time Microsoft did, because yet another report surfaced estimating that only 1.91% of all Windows PCs are fully patched. From Secunia:
98 out of 100 PCs that are connected to the Internet have insecure programs installed!
Number of insecure programs per PC/user:
| 0 Insecure Programs: | 1.91% of PCs | |
| 1-5 Insecure Programs: | 30.27% of PCs | |
| 6-10 Insecure Programs: | 25.07% of PCs | |
| 11+ Insecure Programs: | 45.76% of PCs |
China continues to see more of its citizens flock online, making the .CN TLD now the second most popular TLD, surpassing Germany's .DE, and second only to .COM. Not surprisingly, here in the Security Labs, we see a parallel trend: more malicious Web sites (and malware in general) originating from China. China Internet Network Information Centre (CNNIC) claims the nation's online population grew 41.9% in 2008 to 298 million people (and growing fast). To contrast, the US online population is estimated to be about at 200 million people (and growth has slowed).
Despite the Chinese government's iron-fist-great-firewall-of-China control of their Internet users, the number of bloggers in China reached approximately 162 million by the end of 2008. With blogging now mainstream, as bloggers are now no longer just the early-adopter-amateurs but also professionals representing corporations, the abuse of blogging has also increased. Blog comment spam has now evolved to contain not just the usual visual and attention annoyance, but also malicious code and malicious links to infect the unsuspecting Web visitor.
Slashdot ran a story about botnets intelligently learning, and slowly adapting their tactics (win-loss analysis, anyone?)—bolstering the case made by a separate story about a paper published on Policy Review calling for botnets to be designated as eWMDs.
In other cypherpunk news, security researchers exploited a weakness in MD5 and successfully forged a Certification Authority (CA) certificate. In this study, all modern browsers today would trust any fake site set up by the owners of this "rogue" certificate. MD5's death knell is not earth-shattering—weakness in the algorithm has been the study of many PhDs for years now.
To end this year's This Month in the Threat Webscape blog series, here's a slideshow of the biggest tech crime stories of this past year, from NetworkWorld. Stay informed by subscribing to us (alerts & blogs), or by following our footprints on Twitter. We'll continue to keep you posted on the wicked world of Web threats throughout '09!



























