Archived Blog
Hacker Tool Targeting MS08-067 Vulnerability
11.11.2008 - 9:00 AMBelow is an analysis of the "wolfteeth bot catcher" tool. The original executable file of this tool is named project1.exe, and has been packed to protect itself from analysis. The first step is to unpack the file.
Firstly, the tool drops and runs a backdoor named bycnboy.exe, which moves itself to the system folder and is renamed to windef.exe. This means that hackers who used this tool were themselves hacked by the tool's author. Then a file named project.exe is placed in the temp folder and loaded to run once the original file has finished its job.
The project.exe file in the temp folder has been packed. After unpacking it, we find it places 4 executable files in the temp folder, named 123.exe, MS08-067.exe, s.exe, and Project1.exe.
Next, the project1.exe file in the temp folder is run to show the main GUI.
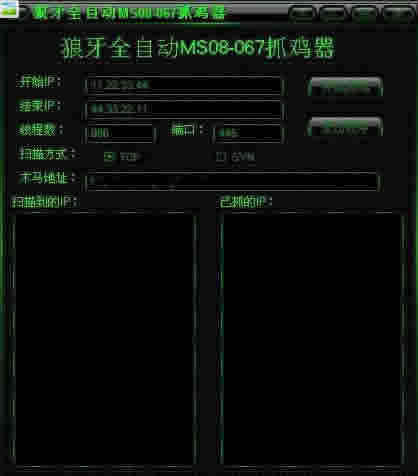
The hacker can then input the network range and Trojan file download URL, and click Start. The file named s.exe is loaded in the command line to scan port 445 in the network range, and return the scanned IP list to project1.exe:
Next, the file MS08-067.exe is loaded to inject a Trojan file to these IP addresses:
Meanwhile, a Trojan file from the user-defined Web site could be downloaded and executed. All the vulnerable IPs are controlled remotely.
Websense will continue to monitor this threat.
Security Researcher: Hermes (Lei) Li



























