Archived Blog
The Blogspot.com malicious blog page:

The malicious code is disguised as ad network JavaScript, which is common on the Internet. In this case, the author of the malicious code uses the same name that Google uses for their ad syndication (show_ads.js).
The Blogspot.com malicious blog page source code: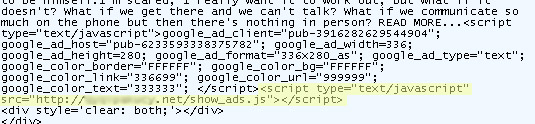
The authors of the malicious code even serve a copy of the real Google ad script if the referrer is not set correctly. This makes investigation into these incidents harder, because the behavior is different depending on the referrer. The authors are looking specifically to avoid detection by Security Researchers, while still affecting the target audience.
The show_ads.js source code with wrong referrer: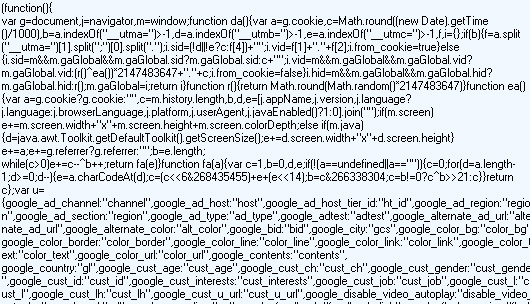
The show_ads.js source code with correct referrer:

You can see the difference in content when the referrer is set correctly. The small amount of JavaScript creates a form, which then does a GET request on what seems to be an JPG file. The form is submitted via JavaScript so no user interaction is required. It is interesting to note that the authors use the process of creating a form via JavaScript and submitting it as their redirection method. Although there are many redirection options, this seems to be a newer method for authors of malicious code.
After the malicious JavaScript has submitted the form to perform a GET on the fake JPG URL, it then bounces around four more times via HTTP 302 redirects. The final destination is a rogue anti-virus (AV) site that tries to install software on your system and performs a fake AV scan.
The rogue AV page: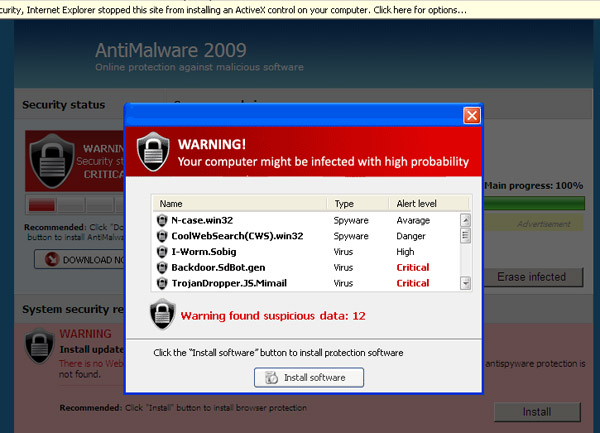
Security Researchers: Chris Astacio and Ali Mesdaq



























