Archived Blog
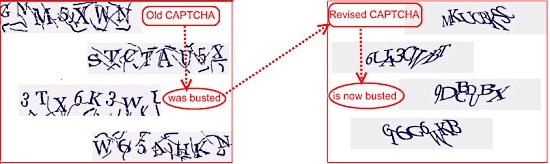
CAPTCHA Revisited: Microsoft's "Revised" CAPTCHA Busted By Spammers For Mass-Mailing Operations
09.30.2008 - 3:00 AMEarly this year (2008), as reported by Websense Security Labs, spammers worldwide basis demonstrated their adaptability by defeating a range of anti-spam services offered by security vendors by carrying out the streamlined anti-CAPTCHA operations on Microsoft's Live Mail, Google's Gmail, Microsoft's Live Hotmail, Google's Blogger, and Yahoo Mail (as reported by InformationWeek).
Realizing the potential for massive abuse from spammers with anti-CAPTCHA capabilities, who could use the clean IP reputation to carry out various attacks over Email and Web space, Microsoft attempted to increase the complexity of their CAPTCHA system. The CAPTCHA system was revised in an attempt to both prevent automatic registrations from computer programs or automated bots, and preserve CAPTCHA's usability and reliability. As this attack shows, those efforts have failed.
Windows Live Hotmail (previously MSN Hotmail and Hotmail) is a free Web mail service provided by Microsoft. Part of the Windows Live brand, Live Hotmail has over 250 million users globally. It is available in 35 languages, and offers 5 GB of storage and integration with Windows Live Messenger, Spaces, and Calendar and Contacts. By registering Live Hotmail accounts, spammers clearly aim to carry out wide range of attacks (both manual and automated) over other services that integrate with Live Hotmail.
There are 3 stages to the automated process (described in more detail below):
Stage 1: Instructions from the CAPTCHA-breaking host injected onto a bot-infected or otherwise compromised machine.
Stage 2: The compromised machine performs the tasks defined in the instructions (received in Stage 1).
Stage 3: A bot begins spamming from the successfully created Live Hotmail accounts.
Stage 1 in action: Instructions from the CAPTCHA-breaking host injected onto a bot-infected or otherwise compromised machine.
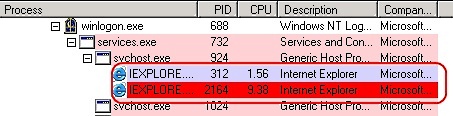
Part 1: The bot installs itself as a service, and uses the Internet Explorer browser on the target machine in the background for the entire process.
Figure 1.1
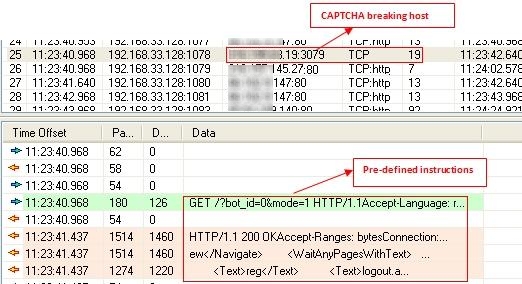
Part 2: The CAPTCHA-breaking host initiates the process of injecting instructions onto the target machine.
Figure 1.2
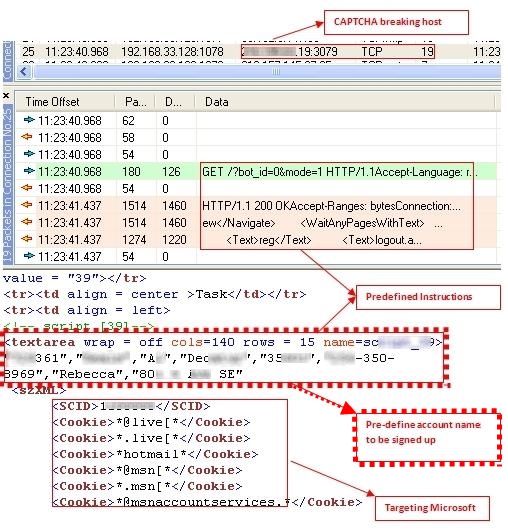
Part 3: Further instructions, with the spammer's credentials, are injected.
Figure 1.3
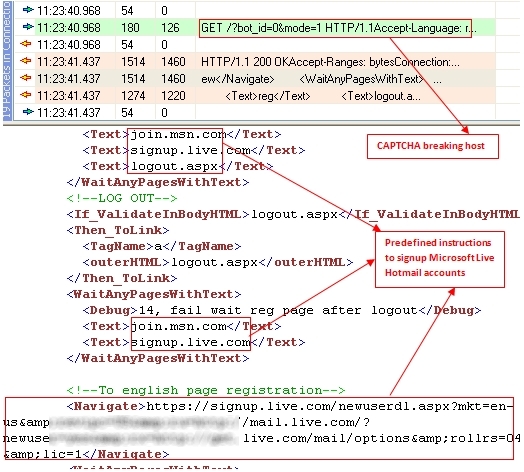
Part 4: Templated signup instructions are injected.
Figure 1.4
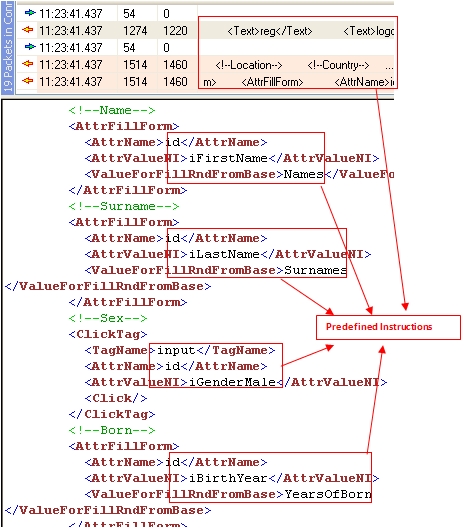
Part 5: Additional instructions to continue the signup process are included.
Figure 1.5
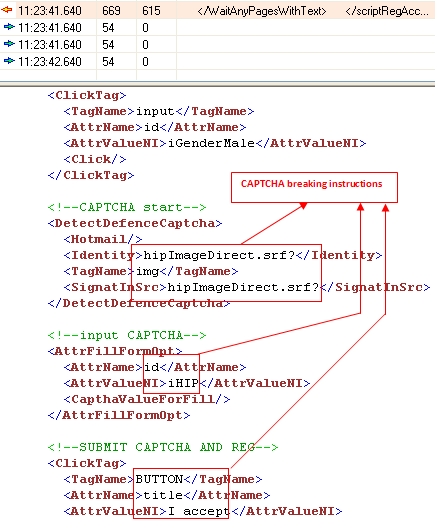
Part 6: The CAPTCHA-breaking instructions are injected.
Figure 1.6
Stage 2 in action: The compromised machine performs the tasks defined in the instructions (received in Stage 1).
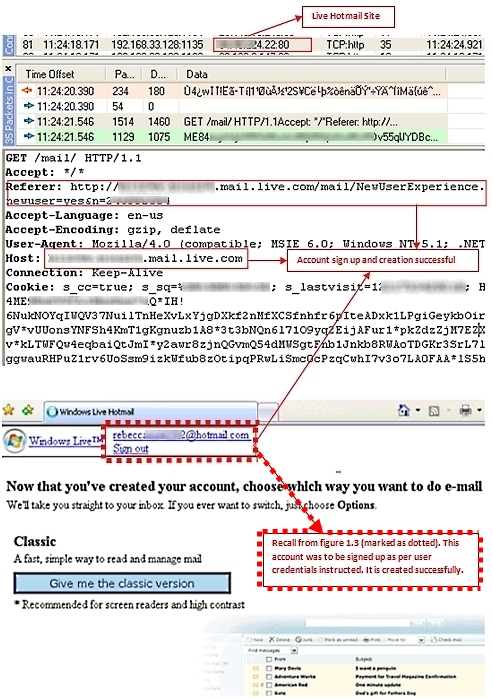
Part 1: A process is initiated on the compromised machine, which connects to the Live Hotmail site to sign up for an account.
Figure 2.1

Part 2: The bot continues to the Live Hotmail secured signup page.
Figure 2.2

Part 3: The compromised machine sends the CAPTCHA image request to the CAPTCHA-breaking host.
Figure 2.3
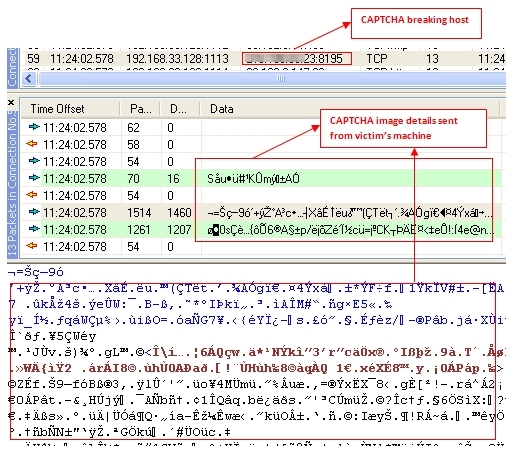
Part 4: The CAPTCHA code is sent (in scrambled format) from the CAPTCHA-breaking host to the compromised machine.
Figure 2.4
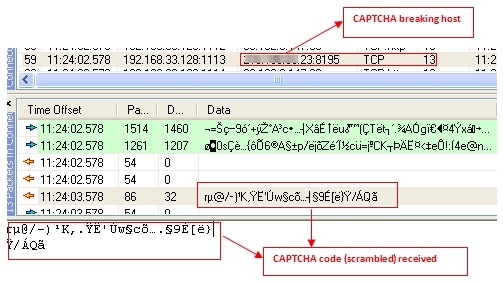
Part 5: The compromised machine descrambles the CAPTCHA code to complete the signup process successfully. You can see that signup is successful and the account is created using the credentials in the instructions injected by the CAPTCHA-breaking host (refer to Figure 1.3).
Figure 2.5
Stage 3 in action: A bot begins spamming from the successfully created Live Hotmail accounts.
Part 1: The bot initiates the process of composing a message.
Figure 3.1

Part 2: The bot edits the email, filling in the "From" and "To" email address lists.
Figure 3.2

Part 3: The bot composes the spam message body (content advertising products and services).
Figure 3.3

Part 4: The bot sends the spam message via Live Hotmail, completing its task.
Figure 3.4

Spam is being sent to targeted accounts!
Here's the process in action:
Figure 5

The spammers successfully advertise their products and services.
Figure 6
Observations:
- One in every 8 to 10 attempts to sign up for a Live Hotmail account is successful (a success rate of 10 to 15%).
- Predefined instructions injected onto the compromised machine are used as templates, and contain various credentials to use when creating accounts.
- Once an account has been created, spam campaigns are sent to multiple recipients in the CC and BCC lists at the same time, with varying message content (themes).
Additional Information:
This latest spambot targeting Microsoft's revised CAPTCHA system includes the combined features of spambots used to target Google's Blogger and Microsoft's Live Hotmail. We reported on these anti-CAPTCHA operations earlier this year (2008). This new attack represents the combined efforts of malware authors and spammers who work constantly to improve attack execution as part of a unified strategy.
In the current attack, the total time required for all of Stage 1 and Stage 2 (injecting the instructions through completing a successful signup) is approximately 20 seconds (as shown below).
Figure 7

Many popular Email, Web and Web 2.0 providers rely on CAPTCHA-based authentication to prevent automated software from performing actions which degrade their function and quality of service, due either to abuse or resource expenditure. From a spammer's perspective, it is a challenge to figure out how to occupy Email and Web space and use them to advertise products and services to prospective customers. In keeping with this mindset, spammers and malware authors have been improving their underground ecosystems to become increasingly adaptable in defending against the continuous efforts made by service providers to combat abuse of their services.
Security Researcher: Sumeet Prasad



























