Archived Blog
Today's blog discusses a nifty tool that helps to solve that problem: FlyPaper, from HBGary.
This tool loads as device driver and blocks all attempts to exit a process, end a thread, or delete memory. All components used by the malicious software will remain resident in the process list, and remain present in physical memory.
When I fire up my virtual machine with FlyPaper and execute a downloader program called foto.scr, the tool does the job: the downloader program shows up in Process Explorer.
Now I can open my favorite debugger and attach it to the downloader to view the memory it uses.
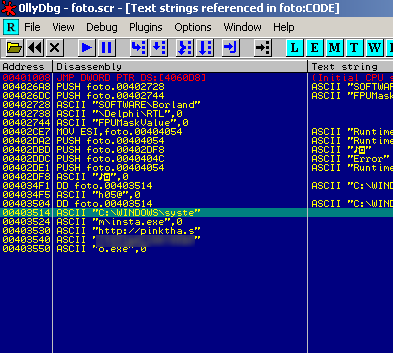
In this example, you can see that the downloader fetches the main malware program from 
Game over!
UPDATE 9/26/2008 - We'd like to thank all our readers for all the feedback we have received. We have blurred out the URL in the OllyDbg screenshot as well, although we *did* intentionally leave it there. By and large, we don't leave malicious URLs directly in text format to prevent people from accidentally CTRL-C'ing and CTRL-V'ing it into a browser. In that image, the URL was broken up enough such that one would have to really piece it together. Some of you had a real sense of humor with your feedback; this is perhaps the best one that we received: Click here for image. Thanks for reading (and the good chuckle!)
Security Researcher: Moti Joseph



























