Archived Blog
CNN and MSNBC Olympic spoof emails - 5 million spam messages per hour
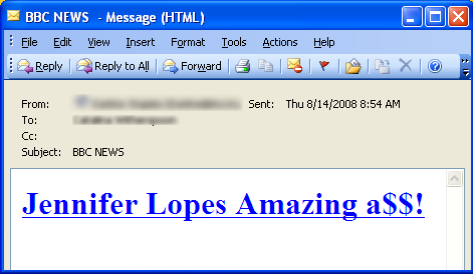
08.14.2008 - 4:55 PMUntil these two recent examples of social engineering with the CNN and MSNBC spoof emails, the illegitimate emails were easy to spot. They simply were one line emails with outlandish headlines. Here is a screenshot of one of the easier to spot news emails. Notice that this one is under the disguise of a BBC alert:
The latest variants of these malicious emails take their social engineering tactic to a new level. They take advantage of trusted brand names to entice end users to click on malicious links. The newest messages are CNN and MSNBC alerts which are edited with more believable stories than the past messages but the link to the stories are replaced with the malicious target links which lead to hijacked Web sites that host the malware.
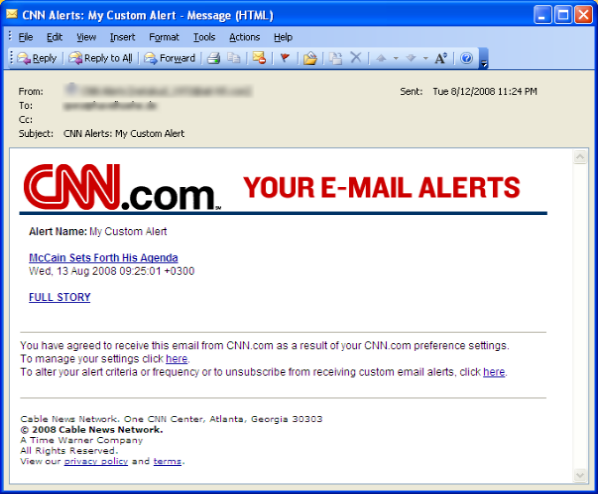
Another dangerous aspect of these CNN and MSNBC emails is the intensity with which the messages have been sent. In this campaign alone, our Threatseeker Network has seen as many as 5 million messages sent, per hour, from multiple hosts worldwide. Here is the screenshot of a malicious CNN alert email:
Here is a screenshot of a malicious MSNBC email:

As stated above, the target links in these messages lead to hijacked Web sites. These sites are hosting the malware, which poses as a missing codec needed to view a video. The malicious links in these messages have either php redirects to the malware, or an HTML page which entices a user to install the malware.
Even though these messages are obviously not being sent by MSNBC and CNN, it is easy for an end user to think otherwise, because the content of the messages looks exactly like the legitimate messages from these news sources. As these messages evolve, it is important to remind end users not to blindly click on links in HTML formatted email.
Rather, if users insist on receiving HTML formatted email, they should always pause their pointer over HTML links before clicking on them to expose the target page and verify if the target is familiar or not. Never click on an email link which leads to an unfamiliar target.
Security Researcher: Chris Astacio



























