Archived Blog
During our research, we found out that it updates regularly and uses various social engineering tricks to spread and infect computers. Various executable components are downloaded, each of them having specific actions, such as spreading the malware, stealing bank information, etc.
The techniques it uses to steal credentials are particularly interesting. One of them is the way it manages to bind fake dialogs from the executable into Internet Explorer, allowing it to "inject" a rogue window into the browser. Visitors will log in and their information will be stolen while the browser still shows the lock at the bottom of the browser. The certificate is still valid, of course, since everything is done on the client side.
Getting Infected
In order to get infected by this malware, people have to execute it themselves. This is where the social engineering tricks come into play. People receive deceptive emails pretending to come from various sources, such as the Ministry of Justice, e-cards, etc. There is always a link to a zip file that people have to follow. Inside of it you have the malware main executable, the one downloading all other components and opening the real page inside of their browser. For instance, if the deceptive email pretends to come from the Ministry of Justice, it opens the real Ministry of Justice Web site.
Here is an example of a deceptive email:

This deceptive email was grabbed from one of the accounts the malware uses later on. The funny thing is, they are all full of spam and deceptive emails, and some of the emails were sent by other email accounts used by the malware. This allowed us to get recent emails, and thus recent Web sites hosting the malware, and therefore updated material. You will see in the next part of this blog how we could access those email accounts, and therefore access all this information.
The Downloader Component
The executable in the zip file is written in Delphi, as are all the other downloaded components. Upon first execution of the downloader, it will make a copy of itself in the \WINDOWS\wdfmgr\ directory. Depending on the version of the malware, the copy has different names. In the case above, it will be renamed to update.exe. The downloader will execute the renamed copy before it exits. Update.exe will then start downloading two SFX rar archives, OUT.JPG and WDFMGR.JPG. Those two files are, in fact, executables and obviously not images.
Both archives actually hold Delphi executables, the actual components of the malware. "OUT" contains "Outlooks.exe" and "packs.exe". The first one has a very deceptive icon, and definitely could look like an email client to unsuspecting computer users. "WDFMGR" contains another WDFMGR executable, this one has an Internet Explorer-like icon and is quite big, about 2.4 MB.
All those components written in Delphi use string encryption in order to hide information from prying eyes. It doesn't really stop analysis; rather, it gives good hints of where to look. Getting the decrypted text takes a matter of seconds, allowing us to quickly go through the malware, and in this case, the downloader component.
You can see on this screenshot encrypted strings in memory during a live debug session:

and what you get when you decrypt them in memory:

Most of those strings are actually related to programs made to protect banks from trojans. Some banks will ask you to install a program in order to protect you from malicious programs.
Outlooks - Spreading Component
One of the executables downloaded is used to spread the malware. Outlooks.exe will download a few text files from a remote Web site: user.txt, mask.txt, assunto.txt.
user.txt actually contains email account information for the infection process.
mask.txt contains the content of the email to send to people you want to infect (html page).
assunto.txt is the subject of the email (there are a few possible subjects).
The screenshot below shows the new deceptive email to be sent. This time it's no longer the Ministry of Justice that is used to deceive people, but rather a fake e-card:

If you click, as stated on the card, you will download another zip file "CartaoVirtual.zip". This zip file has "Cartão Virtual.exe" inside. This is the new downloader component, using a different icon. It's basically the same malware, just updated, using different Web sites, etc. At any given time, they have a few variants in the wild, using different deceptive tricks to get people to run their malicious software.
In outlooks.exe you have plenty of encrypted strings, using the same encryption as the downloader component. You also have plain text strings, and some of them speak for themselves, for example:
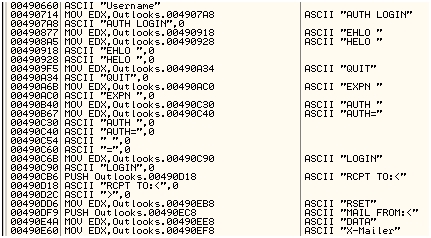
What you see on the above screenshot are SMTP-related strings. The component sends emails using the SMTP protocol and these strings are part of the emailing process. Closely related to this, the user.txt file contains a list of accounts that the malware can use for this infection:

As you can see, we have accounts, SMTP servers, login names and passwords.
Remember the very first screenshot regarding the deceptive email from the Ministry of Justice? Thanks to user.txt, I could log in to the webmail of those accounts and see various infection campaigns used by this malicious app. This allowed me to get more samples and malicious URLs in order to protect our customers from this infection.
Since this blog is already quite long, I will skip the details and go to the actual stealing component.
Banks Stealing Component
This is the most important and interesting component of the malware. As I mentioned in the introduction, this malware is able to bind forms from the malcode executable to Internet Explorer in order to steal information from banks and paypal users. It's almost transparent in some cases. Users have no visible sign of infection unless they make a mistake while entering their information. Indeed, the malware wants to steal information, and therefore makes sure there were no typos or incorrect inputs. It will display a message in Portuguese if a mistake happens:
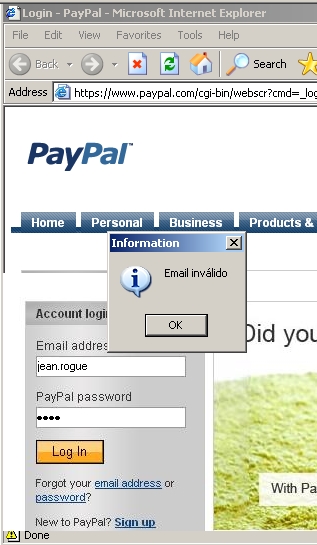
This screenshot shows the rogue form in action. It's all embedded inside Internet Explorer and looks like it's part of the Web page. As you can see, if you don't enter a correct email address, you will get a message in Portuguese, whereas the original page won't show a message like this, especially not in this language.
In order to inject such a rogue frame in the browser, the malware monitors visited pages.

It uses the WWW_GetWindowInfo technique to get the URL. It then uses the URL on various browsers:

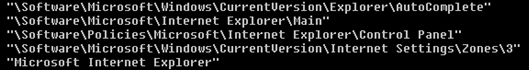
If a bank or paypal is visited, and if the correct URL is visited, then the malware will kill the browser and restart it instantly at the previous page location. It's basically flashing on the screen, depending of how fast the computer is. This is probably to bypass the software banks install to prevent information stealing. Indeed, when the banker component executes, it will update the registry in order to lower the browser security settings. This way, the bank activex apparently won't load and won't protect users:
Once the browser is restarted, the rogue form takes over. The user's information will be stolen and sent using another account embedded in the malware:

There is a login / password for the account used to send emails, and there are two accounts used to receive the stolen information: one in Brazil, and one from Google mail.
As you can see below, the login form doesn't belong to IE, but to WDFMGR, the malware executable:
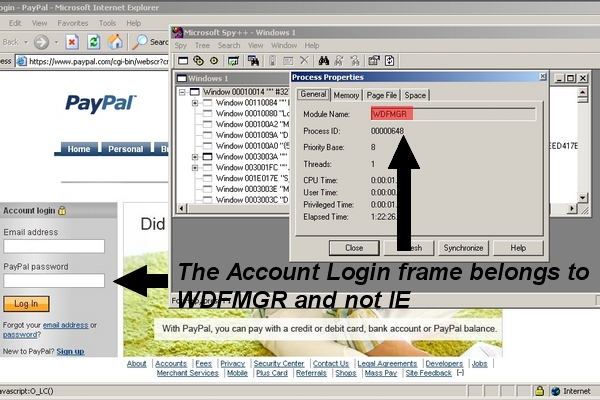
Once you enter the information, you will get another message saying the service is currently suspended. I won't disclose the details on how the frame is taken over, but it's basically related to the "IEFrame" object.
If the page is not paypal, it will check for banks as seen above, and will use various rogue forms to steal information. On this one, for instance, it will display a form using the colors of the bank, and the same virtual keyboard layout, to trick users into inserting their information:

The Internet Explorer layout is all fake. My IE was in English, but was all of a sudden in Portuguese. As you can see, you have the virtual keyboard people can use to log in to their banks, and the malware will steal all that information. It even has checks to make sure you don't enter random information.
I made a video demo of the paypal attack, and you can see it here:
Here stops this journey into a banking trojan. I hope you enjoyed it. I tried to provide as much information as possible, without showing too much assembly line on the propagation and the information stealing. The details on how it manages to bind a form to IE were intentionally not published as we don't want to encourage this sort of practice.
Security Researchers: Nicolas Brulez and Pascal Brulez



























