Alerts
Cyber Extortion Attack
Date:05.23.2005
Threat Type: Malicious Website / Malicious Code
Websense® Security Labs™ has received reports of a new attack that attempts to extort money from users by encoding files on their machines and then requesting payment for a decoder tool.
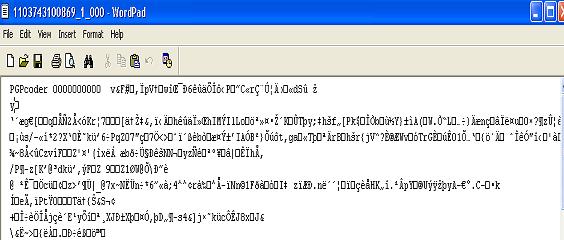
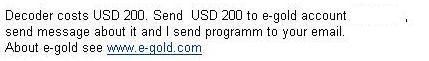
The original infection occurs when the user visits a malicious website that exploits a previous vulnerability in Microsoft Internet Explorer. This vulnerability allows applications to run without user intervention. The malicious website uses the Windows help subsystem and a CHM file to download and run a Trojan Horse (download-aag). The downloader then connects, via HTTP, to another malicious website. This website hosts the application that encodes files on the user's local hard disk and on any mapped drives on the machine. The malicious code also drops a message onto the system with instructions on how to buy the tool needed to decode the files. This message includes the email address of a third party to contact for instructions, and the user is directed to deposit money into an online E-Gold account.
Analysis Details:
• User connects to malicious website that downloads and runs code through Microsoft Internet Explorer vulnerability (http://www.microsoft.com/technet/security/Bulletin/MS04-023.mspx).
• Site drops and runs a Trojan Horse (downloader-aag).
• The Trojan Horse downloader connects to another website and downloads the encoding application, renames it, and runs it.
• The malicious encoding program, which is packed with UPX, performs the following actions upon launch:
-
Adds items to the Windows startup registry: HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
-
Searches for all text files on the computer (including local hard disks and mapped drives).
-
Replaces all files it finds with unreadable content.
-
Creates a status file called “autosav.ini” with information on the files that have been encoded.
-
Creates a file called tmp.bat in the directory where it was run to delete itself upon completion.
-
Creates a file called “Attention!!!” with instructions on how to get your files decoded.
-
Sends an HTTP status request to the server it was downloaded from.
Screenshot 1: (Bin text output on file [after UPX ]) Notice: hard-coded contact details:
Screenshot 2: Screenshot of message with instructions:
Screenshot 3: Example of encoding file:
Screenshot 4: Message with payment details: