Alerts
Targeted Email Examples Relating to Microsoft Internet Explorer 0-day CVE-2010-0249
Date:01.21.2010
Threat Type: Malicious Web Site / Malicious Code
Websense® Security Labs™ has reports that emails linking to malicious web-based exploit code that utilizes the vulnerability CVE-2010-0249 have been sent to organizations in a targeted manner since December 2009, and the attack is still on-going. This same vulnerability was used to target Google, Adobe, and approximately 30 other companies in mid-December 2009. This is a development of the attack we have blogged about previously here.
Investigation has so far lead to the conclusion that these targeted attacks appear to have started during the week of 20 December 2009, and are on-going to government, defence, energy sectors and other organizations in the United States and United Kingdom.
Within the malicious emails the sender's domain is spoofed to match the recipient's domain making the targeted emails more convincing to the recipient. The malicious executables that are delivered by the exploit code include hxxp://cnn[removed]/US/20100119/update.exe or hxxp://usnews[removed]/svchost.exe. These exhibit traits of an information-stealing Trojan with Backdoor capabilities. As of today only 25% of AV vendors protect against the payload according to this VT report.
Example email subjects include:
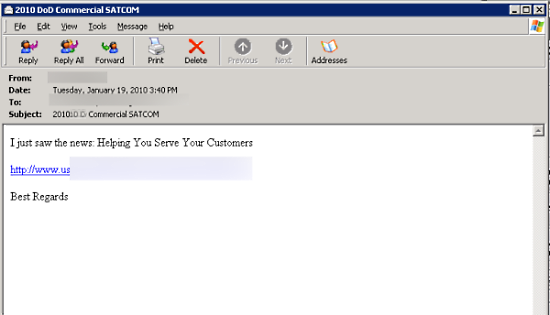
"Helping You Serve Your Customers"
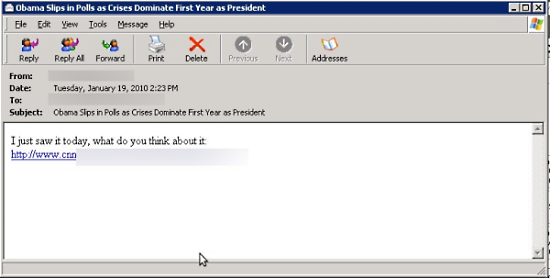
"Obama Slips in Polls as Crises Dominate First Year as President"
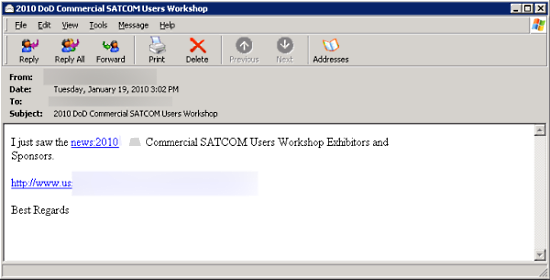
"2010 ***** Commercial SATCOM"
"The Twelve Days of Christmas"
Microsoft has released a patch to address the vulnerability on Thursday 21 January at 10am PST. See MS10-002 summary for details.
Screenshots of targeted emails:

Websense® Messaging and Websense Web Security customers are protected against this attack.


























