Alerts
Microsoft Security Essentials SEO Poisoning
Date:09.30.2009
Threat Type: Malicious Web Site / Malicious Code
Websense Security Labs™ ThreatSeeker™ Network has discovered that search engine results for information on how to download Microsoft's recently released Security Essentials tool are returning links to Web sites that serve rogue AV.
Malware authors have used Search Engine Optimization (SEO) techniques to mix rogue search results in with legitimate results. For example, one of the rogue links is directly under a MSDN blog entry discussing Microsoft Security Essentials. The rogue redirects are hosted on compromised Web sites, including a Canadian publisher's Web site and the British Travel Health Association.
When a user browses to the compromised Web sites, so long as they have been referred by a search engine, they are redirected to malicious Web sites with domain names such as computer-scanner21 and computervirusscanner31.
An example of one of the payload files shows that AV detection is low. One such file is named Soft_71.exe (SHA1: 4e58a12a9f722be0712517a0475fda60a8e94fdc)
If the user downloads the application, a file with extension .tif is downloaded in the "program files\TS" directory as TSC.exe and system.dat (the .tif file is decrypted/decompressed and split).
The payload then executes "tsc.exe -dltest" apparently connects to a NASA Web site, to check internet connectivity.
Finally, "tsc.exe" is executed with no parameters, and the rogue AV starts. (In the background the original file is deleted).
Since yesterday the Websense ThreatSeeker Network has been monitoring SEO poisoning of search terms related to Microsoft Security Essentials. It appears that the malware authors set up a trial run of SEO poisoning techniques, before converting the redirects to deliver rogue applications today.
Screenshot of Google search results:
Screenshot of rogue AV Web site:
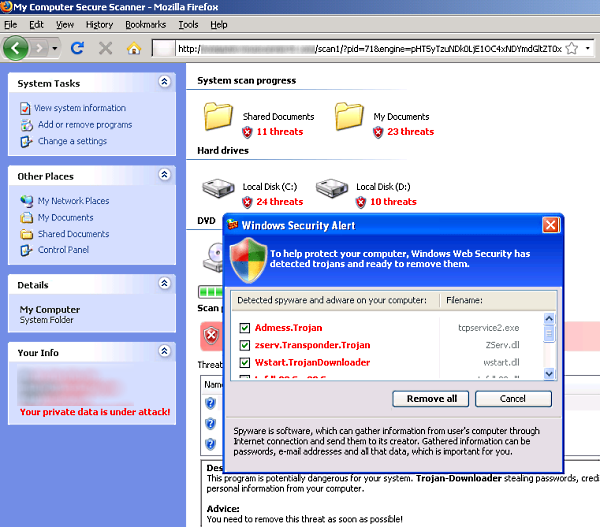
Screenshot of download prompt:

Websense® Messaging and Websense Web Security customers are protected against this attack.


























