Alerts
Mass Injection - Nine-Ball Compromises more than 40,000 Legitimate Web sites
Date:06.16.2009
Threat Type: Malicious Web Site / Malicious Code
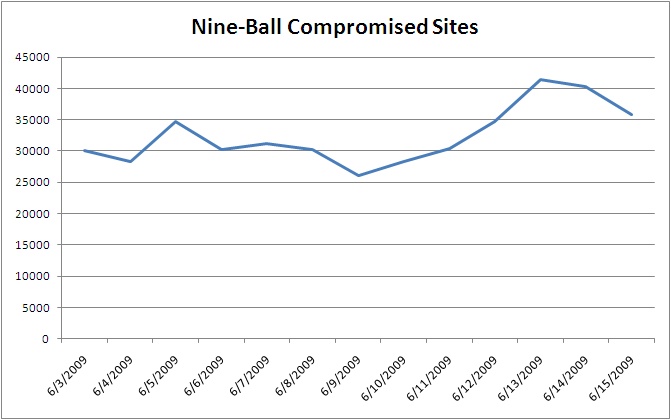
Websense Security Labs™ ThreatSeeker™ Network has detected another large mass injection attack in the wild after the Beladen and Gumblar attacks. We are calling this mass compromise Nine-Ball because of the final landing site. We have been tracking the Nine-Ball mass compromise since 6/03/2009. To date, over 40,000 legitimate Web sites have been compromised with obfuscated code that leads to a multi-level redirection attack, ending in a series of drive-by exploits that if successful install a trojan downloader on the user's machine.
Number of infected Web sites:
If a user visits one of the infected sites, they are redirected through a series of different sites owned by the attacker and brought to the final landing page containing the exploit code (the redirection path is shown below). The final landing page records the visitor's IP address. When visited for the first time, the user is directed to the exploit payload site. But when visited again from the same IP address, the user is directed to the benign site of ask.com.

The obfuscation code injected into these legitimate Web sites is somewhat random, but the deobfuscation algorithm is consistent amongst all the infections. The algorithm uses the JavaScript method "String.fromCharCode" to convert a chunk of decimal values to a string. The string obtained after deobfuscation is an iframe that eventually leads to an exploit site. Here is an example of an injected site:

After redirection, the exploit payload site returns highly obfuscated malicious code. The malicious code attempts to exploit MS06-014 (targeting MDAC) and CVE-2006-5820 (targeting AOL SuperBuddy), as well as employing exploits targeting Acrobat Reader and QuickTime. The MS06-014 exploit code will download a Trojan dropper with low AV detection rate. This dropper drops a dll with the name SOCKET2.DLL to Windows' system folder. This file is used to steal user information. The malicious PDF file, served by the exploit site, also has very low AV detection rate.
Websense® Messaging and Websense Web Security customers are protected against this attack.


























