Alerts
Reverse Vishing in China
Date:09.05.2008
Threat Type: Phishing Alert
Websense® Security Labs™ ThreatSeeker™ Network has discovered a developing "reverse Vishing" attack in China.
The attackers have been posting to BBS fake telephone numbers against the names of legitimate organisations in an attempt to associate those numbers with the customer support numbers for famous Web properties. The use of search engine optimisation (SEO) poisoning techniques in this manner shows the increasing sophistication behind traditional telephone lottery scams. If users search for customer support information, the highest ranking Web sites are returned in Baidu or Google search results with the fake phone numbers.
The attackers are using this in two ways. First, they send out spam email suggesting the recipient has been successful in a lottery. Before sending on the requested contact details the user would wish to verify these claims. Upon conducting a search in popular search engines, the user would see the association of fake telephone numbers with the customer support details.
Second, the high-cost telephone numbers are an additional revenue generator for the scam artists, and they add a layer of authentication to the scam. Unlike traditional Vishing where automated voice sytems call the victims in order to gain information this attack prompts uses social engineering to prompt the user into calling the fraudalent phone line. As of this morning, our China-based Security Labs team has proven the fake telephone numbers are still active. The messages provide details to convince the user the lottery fund is genuine.
As we have found so far, most of these numbers belong to the Hainan province in China. Many high profile names like Sina, Taobao, QQ, Tencent, etc., from portal sites to shopping sites, have been used as part of the attack. Dozens of fake telephone numbers are being used to lure users into dialing. This makes association with a single attack source more difficult. The scam artists post these fake phone numbers to some popular BBS and message boards because those BBS and message board Web sites have a high ranking returned in search engine results.
An example blog spam post to a high profile forum:

To illustrate the scale of the blog spam / comment spam technique used in this attack, Google and Baidu are currently indexing tens of thousands of Web sites containing the fraudulent telephone numbers.
Screenshot of the search results in the first page of Google:
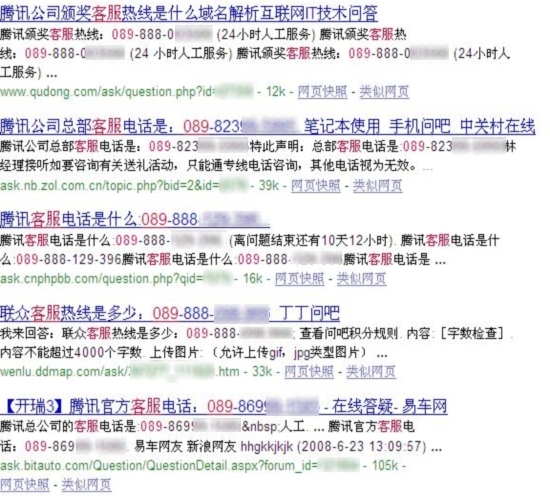
Screenshot of the search results in the first page of Baidu:

Websense Web Security customers are protected against this attack.


























